Watch the best security videos on SSW TV for free.
The 10 tips CEOs must know for both end-users and SysAdmins:
If you need to remember the password then a passphrase is best. Preferably these should be made up of 4 random words with a length of at least 16 characters. These eliminate the requirement for special characters and are incredibly difficult for a computer to guess.
A strong password would look something like this:
correcthorsebatterystaple
🙂 Figure: OK example - A strong memorable password
However the best passwords in the world are the ones you can never possibly remember. Computer generated passwords, with a length of at least 16 characters, offer the most protection. A super strong password looks something like this:
$Jun!ZW@gYS%bmy0($34hYj&8hsgfDF
✅ Figure: Good example - A strong computer-generated password
This is obviously not something you can realistically type in every time you need to use it. Fortunately, the same tools that generate these for us also manage them, storing them securely and automatically entering them into websites and apps for us.
With a password manager, you don't have to remember that strong, unique password for every website. The password manager stores them for you and even helps you generate new, random ones.
The best way to protect your passwords is to never share them. However, in some cases, sharing passwords may be necessary. In these situations, it is essential to follow a strict password sharing procedure to ensure the security of sensitive information. The key to this procedure is having a powerful password manager to be able to share passwords securely and efficiently.
Often an organization needs to share a password to a 3rd party. Perhaps a client or a vendor require a password. There are a few ways that this could be achieved but some are less secure than others.
Keeping sensitive details like credit card numbers and passport information in unsecured places is risky. It can harm both the individuals involved and the organization’s reputation.
Ideally, avoid storing this information altogether. However, that is not always practical. Managers and CEOs often need to share these details with admin staff to book flights or arrange travel, for example. When that happens, make sure the information is stored and shared securely. Use encrypted files, password managers, or secure portals instead of emails, spreadsheets, or notes.
Microsoft is constantly releasing updates for Windows and one of the most important things they do is patch viruses. Without these updates, users would be vulnerable to attacks from hackers. This is the same for MacOS.
So it is critical to always keep your operating system up to date.
Often users don't know how to properly secure their computer and open themselves to vulnerabilities. Windows Security solves this by ensuring that a PC is running all the best practices to keep it safe from harm.
Users are often exposed to viruses on their machines. Virus scans help identify and remove potential threats on your machine. Windows comes with built-in protection called virus and threat protection that is suitable for most situations.
Complexity requirements are valuable in that they offer a little protection, but not as much as you think. Attackers generally use 2 methods to get people's passwords: brute force, and social engineering.
Passwords are a legacy technology that is not fit for the purpose that we use them today. We're working our way towards a post-password world, in particular the FIDO alliance, and many biometric technologies, including fingerprint and face recognition that you may have in your phone. But for now, passwords are something we all need to live with.
Minimum password age and maximum password age rules are not useful and do more harm than good. Passwords are already difficult to manage, and forcing people to change them at specific times encourages poor password practices, such as using well-known transforms and substitutions, or writing them down.
The available list of 10, 12, or 16 (or better yet in terms of length, 20) character words is limited. So if you pick one of these words you don’t afford yourself much protection.
Possible combinations of words, or phrases as we call them, are almost infinite. While we still use the term ‘password’, you should use a short phrase rather than a word.
Note: Ideally you should not need to remember any password, instead use a password manager.
Using the same password for multiple accounts or services can pose a significant security risk. It's a common mistake that many people make, but understanding the importance of unique passwords is crucial for safeguarding your online accounts.
Most people might be unconcerned, saying that there was little to panic about if someone had compromised their LinkedIn account. But if you ask them “but what about every other website you use the same username and password for?” they would often go pale and run to their computer to check.
Using the same password everywhere may seem like a convenience, but the impact of a compromised password can be orders of magnitude greater if you reuse it.
Employees with a compromised account should immediately contact their SysAdmins for help. This is whether it is a personal or a work account.
A personal account (e.g. Gmail) breach should be resolved by a System Administrator with the same priority as a work account. Employees should expect the same level of service on a personal breach as you would on a corporate breach.
Why? If your Gmail has been hacked this can have implications for the company.
Once you have informed your Systems Administrator of a potential breach send an "As Per My Conversation" email.
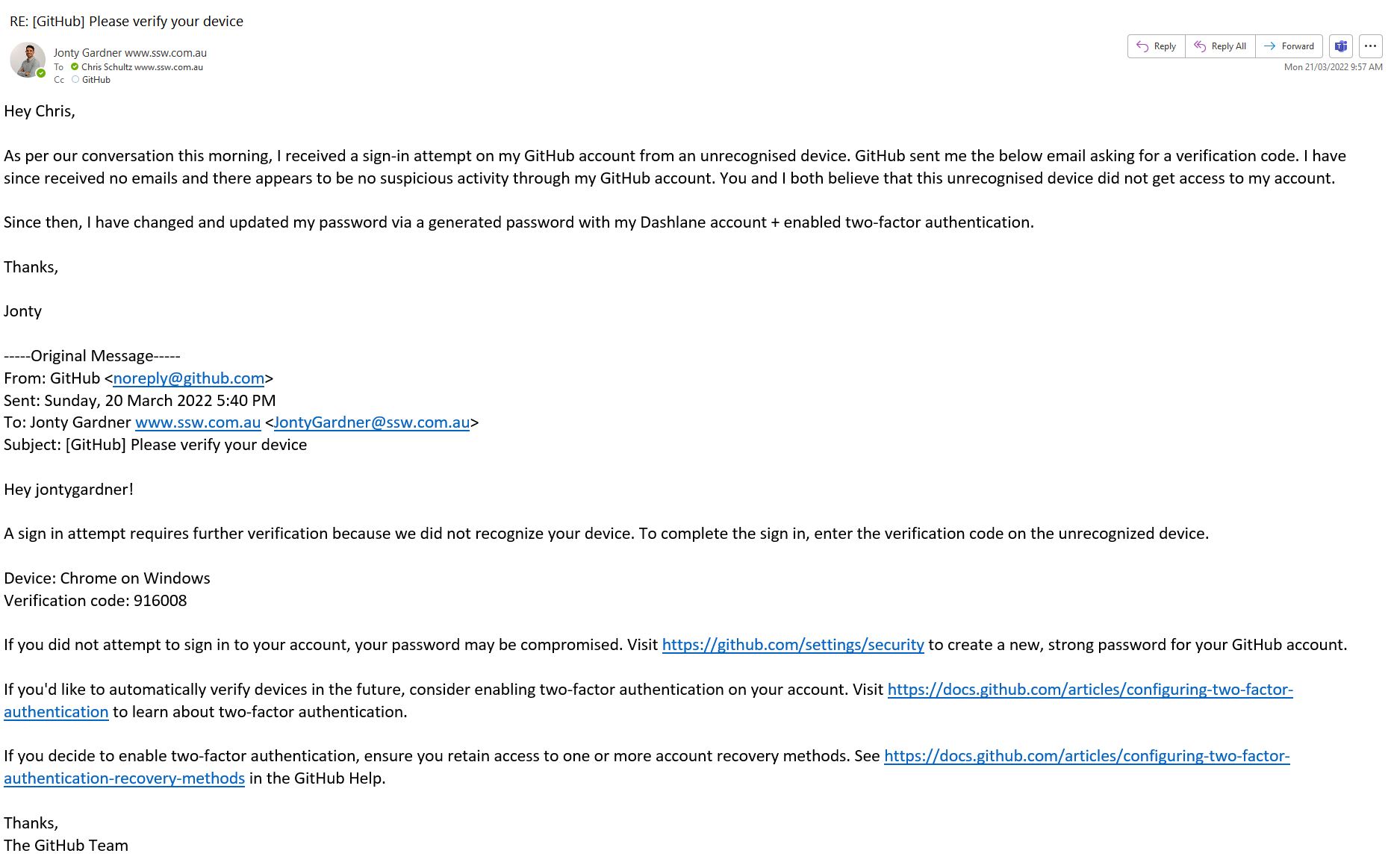
✅ Figure: Good example - Inform the SysAdmins of a potential breach
The best protection you can provide for your password is to not solely rely on it. Multi-factor authentication (MFA) lets you use a mix of techniques when logging into an account. Typically this is made up of something you know (your password) and something you have (your phone - older people will remember RSA tokens).
Read the article Best Ways to Keep your Recovery Phrase Secure.
Sometimes passwords can be compromised through no fault of our own. There have been several high-profile breaches of password databases.
The project haveibeenpwned is a free database that aggregates data from breaches, and you can use it to check whether your account has been included in a known breach.
When an organisation has a security breach, passwords are compromised and there is no visibility of the problem. This problem means that hackers can gain access to people's accounts without anyone realising what has happened! The project haveibeenpwned is a website that addresses this problem...
The most common attack vector for hackers to either compromise our computers or deliver malware is email. Some of these attacks are sophisticated, perpetrated by well-funded criminal organizations. But these are rare, and usually targeted at a specific individual for a specific purpose.
Phishing is a form of social engineering where an attacker tries to convince a victim that a resource they are in control of is a legitimate resource. This is usually achieved through the use of deceptive email messages or websites.
Attackers will often craft a website that looks like a legitimate one for the sole purpose of stealing your username and password (or some other sensitive information). They might, for example, build a website that looks exactly like LinkedIn, so that you think you are logging into LinkedIn, but are in fact giving an attacker your username and password.
per page
1 - 20 of 22 itemsper page
1 - 20 of 22 items