Do you store your GitHub secrets in Azure KeyVault?
Last updated by Brady Stroud [SSW] 5 months ago.See historyWhen creating pipelines for a company there is often secrets that need to be used by more than 1 repository. This is something that GitHub can't do natively. A developer is also unable to read the secrets in GitHub once they are entered. Although this is for security a simple typo can't be found and instead the entire secret needs to be reentered. There is also no visible history for GitHub secrets and no ability to revert to an earlier version of a secret.
Solution: Store them in Azure KeyVault.
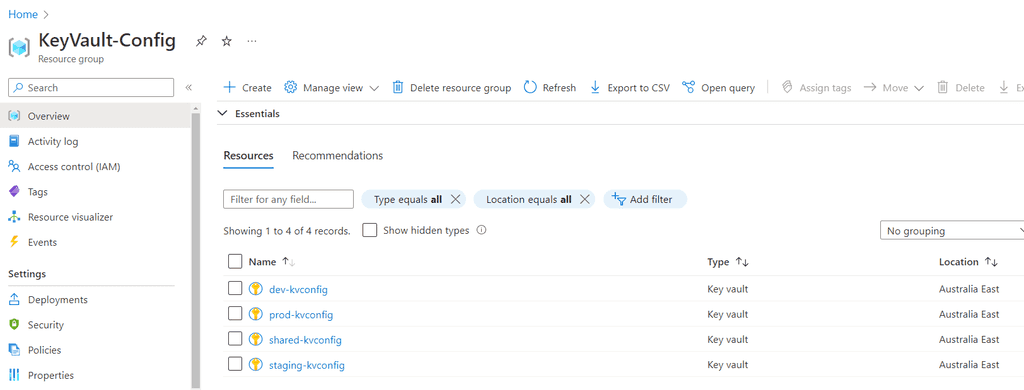
Create the KeyVaults
- Create a seperate Resource Group in Azure
- Add 1 x shared KeyVault - These will store any values that would be the same no matter which environment you are deploying to.
- Add 1 KeyVault for each environment you will deploy to - These are to store any values that are specific to the development environment (i.e. dev, staging, prod)
Use the KeyVaults in your CICD pipeline
- In a GitHub action use the following code:
- name: Azure CLI script
uses: azure/CLI@v1
with:
inlineScript: |
az keyvault secret show --vault-name dev-kvconfig --name myAppInsightsKey --query valueFigure: Retrieve KeyVault Secrets to use in GitHub Actions
- Bicep - In the file that you wish to use a secret add this code:
resource environmentKeyVault 'Microsoft.KeyVault/vaults@2022-07-01' existing = {
name: '${environmentName}-kvconfig'
scope: resourceGroup(envSubscriptionId, envResourceGroup)
}Then reference the value like this to provide parameters for other bicep modules:
module azuredeployment 'environment-keyvault.bicep' ={
name: '${projectName}-${lastDeploymentDate}'
scope: resourceGroup()
params: {
location: location
tags: tags
AppInsightsKey: environmentKeyVault.getSecret('myAppInsightsKey')
}Figure: Retrieve KeyVault Secrets using Bicep
- PowerShell - Access the same secrets directly from PowerShell:
Get-AzKeyVaultSecret -VaultName "$environmentName-kvconfig" -Name myAppInsightsKey -AsPlainTextFigure: Retrieve KeyVault Secrets using PowerShell