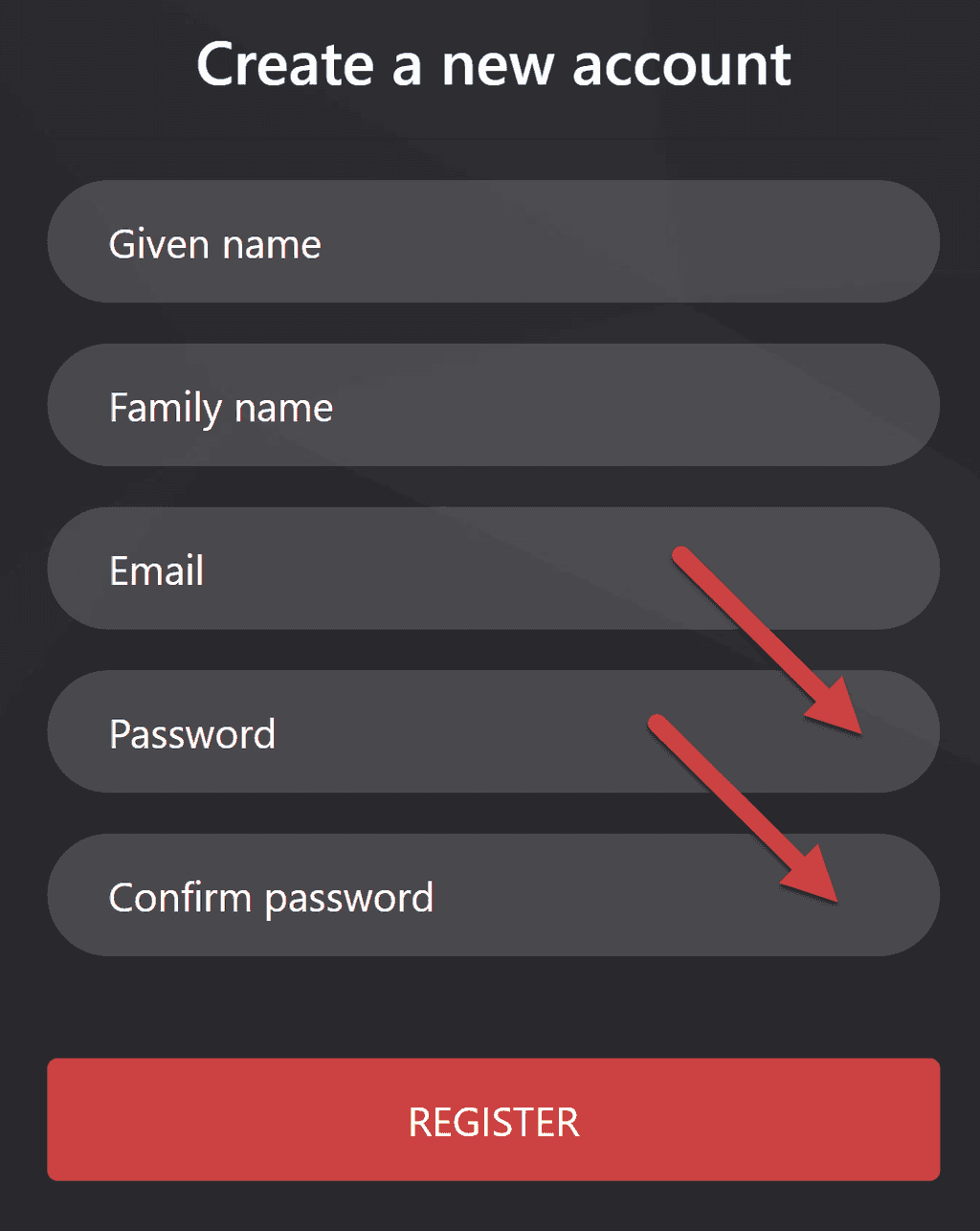
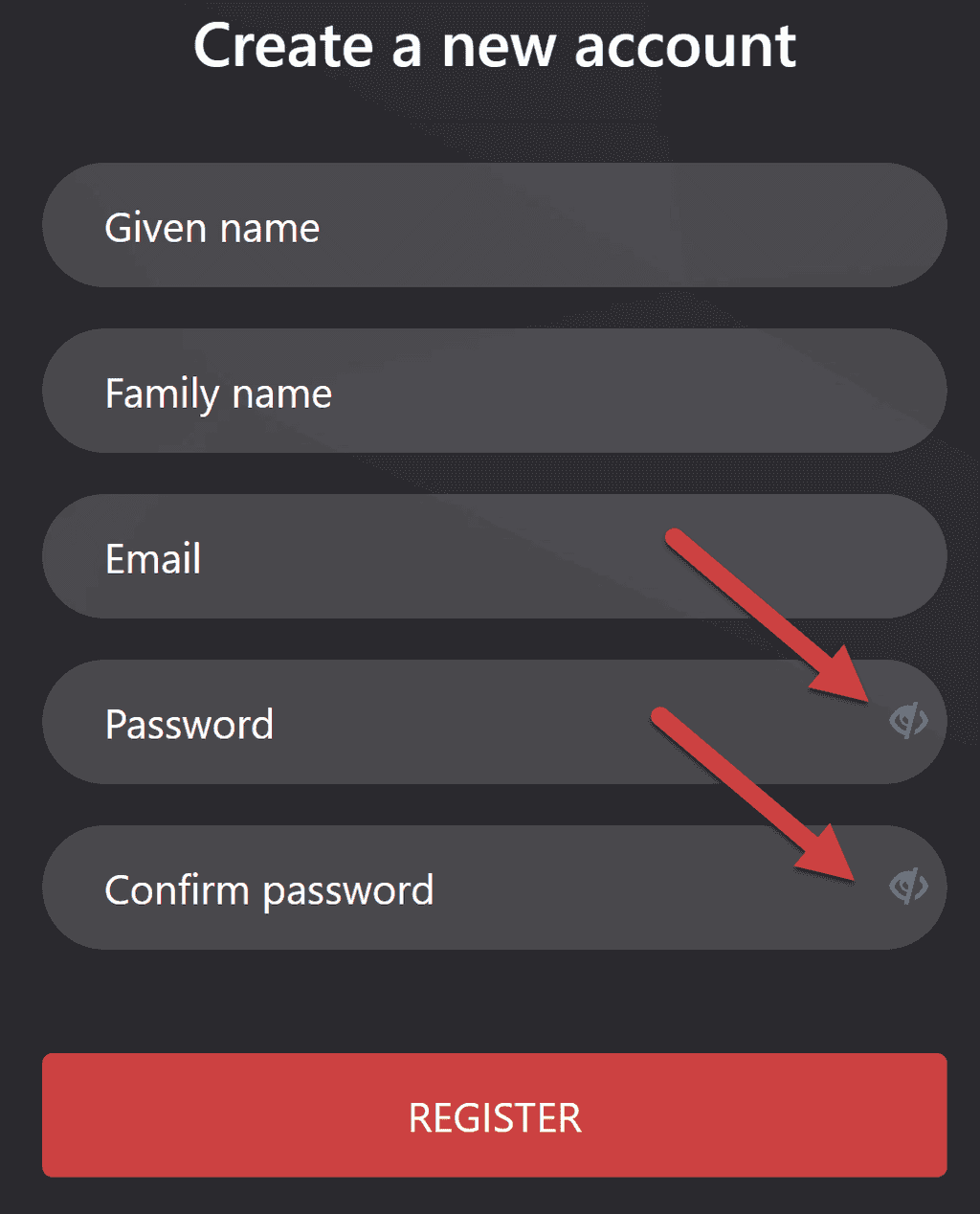
Rules to Better Security - 32 Rules
Want to avoid embarrassing or expensive data breaches? Check SSW's Security consulting page.
Watch the best security videos on SSW TV for free.
Authentication and authorization are complicated, and it is risky to try and implement them yourself. Use this rule as a guide on choosing the right service or framework for your situation.
Choosing the right authentication and authorization approach for your situation can be tricky. It is a multi-faceted problem with many variables, and what seems like the right choice in one situation may not be in the other.
Start with the questions
- Scope - Is it an enterprise application for internal users or a consumer application for external use?
- Scope - Do you need to share the identity across multiple applications?
- Volume - Do you have an estimate for how many users you need to support?
- Complexity - do you need to execute arbitrary logic (see below) as part of your authentication process?
Without the answers to these questions, it will be difficult to choose the right option. With the answers to these questions, you can use the tips and flow chart below as a guide to help you choose the right solution.
'Complexity' in authentication
Most applications require some form of authentication, and it's often as simple as providing a secure way for users to log in and ensure that unauthenticated users don't get access to protected resources. However, it's not uncommon to require some logic to be executed as part of the authentication process. Some examples might include:
- Querying an application to get a list of a user's roles
- Calling an API to check a conditional access policy
- Registering a user with an application during sign-up
- Integrating a technology that is not included out of the box (e.g. WebAuthN)
- Non-standard integration with an upstream identity provider
Note that some of the options listed below support or include the features listed above, and these may be configurable directly rather than needing additional code or logic to support. These usually come with additional costs. When you need one of these that is not provided "out-of-the box", you need to build this yourself. Most of the options listed here provide a way to inject custom arbitrary logic into the authentication process, but they have different ways of achieving this and varying limitations.
Narrow your options
Each project is different, and you will need to consider your individual needs and circumstances when choosing how to implement identity and authentication in your solution. There are countless options available for authentication, but the chart below can provide a guide for some of the major decisions, and help you narrow down to some of the relevant options. Use this to get started and be sure to consider all the other information in this rule before making a decision.
flowchart Start(["Start"]) --> CustomLogic{"Need Custom/\nComplex Logic?"} CustomLogic -->|"Yes"| IdentityServer(["IdentityServer"]) CustomLogic -->|"No"| AppType{"Application Type?"} AppType -->|"Internal (Intranet)"| Kerberos{"Need Kerberos/\nAD Integration?"} AppType -->|"External (B2B/B2C)"| Hosting{"Hosting?"} KerberosHosting{"Hosting?"} -->|"On-Permises"| SingleApp{"SSO?"} KerberosHosting -->|"Cloud"| Ecosystem{"Existing Ecosystem/\nPreference?"} Kerberos -->|"No"| KerberosHosting Kerberos -->|"Yes"| OnPremAD(["On-Premises Active Directory"]) Hosting -->|"On-Premises"| Kerberos Hosting -->|"Cloud"| Ecosystem Ecosystem --> Entra(["Entra ID"]) Ecosystem --> Auth0(["Auth0"]) Ecosystem --> OtherIDP(["Other Cloud IDP"]) SingleApp -->|"Yes"| IdentityServer SingleApp -->|"No"| NETCORE(["ASP.NET Core Identity"])Figure: Authentication Selection
Your situation is unique, and every application's requirements are different. These tips can help you identify options to consider for your solution.
Additional considerations
In addition to the main points discussed above, the following considerations could also be relevant to your decision.
❗ Always important
- Scalability: Depending on the expected user base and request volume, scalability can be a concern. Some solutions might offer better scalability options than others
- Cost: The costs associated with different solutions can vary. It's essential to consider both initial setup costs and ongoing operational costs
- Maintenance & Support: How easy is it to maintain the solution? Is there good community or official support available? This can be crucial for troubleshooting and ensuring the system remains operational
⚠️ Important - but depends more on your needs
- Regulatory & Compliance Needs: Depending on the industry, there might be specific regulatory or compliance requirements related to authentication. For example, financial or healthcare industries might have stricter requirements
- User Experience: The ease of use for end-users can be a factor. Some solutions might offer a smoother user experience, fewer login prompts, or better integration with other services
- Flexibility & Extensibility: How easy is it to extend or modify the authentication process in the future? This can be crucial if there's a need to add new features or integrations later on
- Security Features: Beyond MFA, what other security features do the solutions offer? This can include things like anomaly detection, risk-based authentication, or integration with threat intelligence services
While there are too many options to cover them all, this chart will help you narrow your choice to a few key options. Some detail about these options is provided below.
1. ASP.NET Core Identity (simple and free)
ASP.NET Core has some built-in identity functionality that allows you to create users and roles, and manage the security of your web applications. It is extremely capable and can be used to support a broad number of scenarios. However, it is intended for use in simple web applications, and while it can be extended to support other clients, you will need to build and wire up a lot of the UI for these scenarios yourself.
With the new Identity endpoints in .NET 8, you can now support even more scenarios (like using API endpoints to exchange a username and password for an access token).
However, the most important consideration is that this approach is intended for use in a single, standalone application.
Your identity store will be limited to this one application, so your users will not be able to share this identity across multiple applications.
Advantages:
- Free
- Easy to set up and use
- Supports OAuth2/OIDC providers
Disadvantages:
- It is recommended by Microsoft that for advanced requirements you don't use this on its own - so need to add one of the below
- Does not scale across multiple applications - so need to add one of the below
-
For anything other than an ASP.NET Core Web app (e.g. Angular, React, or mobile), you have to build all UI yourself, such as: sign up, log, password reset, etc.
- Note: You will need to build this UI yourself anyway if using Identity Endpoints.
Use this option if...
- You need to add identity to a simple ASP.NET application
2. IdentityServer (full control)
Identity Server is an open-source, OIDC compliant solution that is built on top of ASP.NET Core. It has extensive support for a number of authentication and authorization scenarios and supports multiple external identity providers out of the box (meaning it can easily integrate with Microsoft, Google, etc. accounts). IdentityServer extends ASP.NET Core Identity to natively support multiple client types (e.g. web, mobile, machine-to-machine, etc.) and can be used as a single identity across multiple applications.
IdentityServer provides unmatched flexibility and control over your authentication process. While some other options provide ways to execute custom logic as part of a login process, for anything beyond the most basic of scenarios, IdentityServer will be orders of magnitude easier to implement.
By running your own IdentityServer, you can provide and manage your own SSO IDP across multiple applications.
Advantages:
- Inexpensive
- Allows you to define custom authentication logic (see 'Complexity' in authentication above)
- Supports multiple applications/identity consumers
- Supports multiple clients and client types
- Fully OIDC compliant
Disadvantages:
- Learning curve
- Requires additional hosting resources
- Requires additional skill set
- Requires ongoing maintenance
- Annual license fee
Use this option if...
- You need to inject custom logic into your authentication flow, or:
- You have compliance requirements that prohibit you from using a cloud IDP
3. OpenIddict (extend to build your own auth)
OpenIddict is an open-source framework designed for ASP.NET Core that facilitates the implementation of OpenID Connect (OIDC) servers. Whereas IdentityServer provides a full solution, OpenIddict provides a foundation upon which you can build your own IdentityServer-like product.
Out of the box, it provides support for all of the core OIDC functionality (i.e. granting and validating tokens), but does not provide any UI or user management, or any way to manage clients, resources, scopes etc.
Because of this, it provides even more flexibility than IdentityServer; but this comes at the cost of taking on a significant implementation overhead yourself (it's like saying buying a bunch of car parts provides more flexibility than buying a car).
Advantages:
- FOSS
- Fully OIDC compliant
- Enables you to build your own identity solution without having to rebuild the fundamentals
Disadvantages:
- You have to do nearly everything yourself
- Significant maintenance overhead
- Requires significant security expertise
Use this option if...
- You are time rich and money poor, and/or:
- You can commit substantial well-skilled (in security and development) human resources to building and maintaining it, and/or:
- You are intending to build your own authentication product
4. Active Directory (for Internal Enterprise Applications)
Active Directory has been the de facto enterprise identity store for most of the world for decades. While most organizations are moving to the cloud these days, many still use AD as it provides a lot of additional capability and is integrated with most of their existing enterprise applications. AD supports multiple authentication protocols, including:
- LDAP/LDAPS: simple to use but old tech, requires multiple queries to check permissions, roles not natively supported, and need to be managed by groups.
- Kerberos: Excellent experience for users as it provides a silent and transparent login. But can only be used for on-premises, domain-joined computers.
- ADFS/SAML: Modern application authentication against AD is done via ADFS with SAML. This is often extended through third-party tools such as Okta to support applications that use JWT and claims.
- Proprietary Microsoft: Basic, NTLM, etc.
Advantages:
- Already in place in most enterprise organizations
- Users do not require an additional identity
- Can make the application compliant with the organization's existing security policies
Disadvantages:
- Not suited to external use
- Not natively supported off-premises
- No MFA included
Use this option if...
- Your application, domain controllers, and clients are all on the same network, and:
- You already have AD in place and have a security policy that states that all your users must authenticate against your centralized corporate identity, and/or:
- You want to enable pass-through/silent authentication for your users
5. Microsoft Entra ID (previously Azure AD) (for Internal Enterprise Applications)
Microsoft Entra is Microsoft's cloud-based identity and network/access management platform and provides strong identity features such as MFA and self-service password recovery, as well as access policies and anomoly detection. Being cloud-based, it can authenticate users anywhere in the world (rather than just on-premises on corporate computers).
Advantages:
- Many organizations already using it
- Extends existing enterprise identity to the cloud (i.e. is supported off-premises)
- Can be used to ensure compliance with existing company security policies
- MFA support included
Disadvantages:
- Can be costly for features not in the free tier
- Requires a skilled Azure SysAdmin to manage
Use this option if...
- You want to support internal/enterprise users, and:
- You already have Azure set up, and/or:
- Your users require access from off-site, and/or:
- You need to enforce MFA
6. Microsoft Entra External Id (previously Azure AD B2C) (simple Auth as a Service)
Microsoft Entra External ID has replaced AAD B2C. It's part of the Microsoft Entra family and includes all the benefits it provides, as well as enabling consumer-friendly features. These include integration with external identity providers and more flexible/customizable login flows. It is well-tailored to support authentication, and while it can be extended to support additional capabilities, this requires custom development.
Advantages:
- Inexpensive and generous free tier
- Native support for multiple external auth providers
- MFA support included
- Relatively straightforward to setup
- Ongoing security maintained by Microsoft
Disadvantages:
- Very limited flexibility
- Can support roles and other extended functionality, but requires significant development
Use this option if...
- You want to support MFA, and/or:
- Your users are external/consumers, and:
- You anticipate a high volume of users, and/or:
- You only require simple authentication and limited or no authorization
7. Auth0 (sophisticated Auth as a Service)
Auth0 is a commercial identity product aimed at developers. It is cloud-hosted and offers out-of-the-box functionality for user signup and login, self-service password recovery, OIDC compliance, external auth integration, and other consumer and user-friendly features. MFA is supported out of the box, and significant sophisticated functionality is available on the paid tiers.
Advantages:
- Good free tier
- Very easy to set up and use
- MFA support included
- Supports multiple external auth providers
- Significant extensibility
Disadvantages:
- Free tier is more limited in volume than competition (e.g. Microsoft Entra External ID)
- Free tier only includes the basic functionality (same as Microsoft Entra External ID)
- Free tier only supports 2 social identity providers
Use this option if...
- You want to enforce MFA, and/or:
- Your users are external/consumers, and/or:
- You require authorization or complex authentication
8. Okta (for Commercial Enterprise Applications $)
Okta is a commercial identity product aimed at enterprises. Many enterprise-centric software products, for example, Salesforce, have Okta connectors. Okta is intended to bridge the gap between enterprise authentication (such as AD) and modern software and SaaS products.
Advantages:
- Integrates with anything
- Very well supported in the enterprise
- Can simplify integration with AD
Disadvantages:
- Expensive
- No free tier
- Not suited to consumer-facing scenarios
Use this option if...
- Your application is for internal/enterprise users, and:
- You already have Okta in place, and/or:
- Your application is a product that you intend to commercialize (Okta is prevalent in the enterprise and having an Okta connector is a good selling point)
9. Keycloak (Open-Source IAM Solution)
Keycloak is an open-source identity and access management solution created in 2014. Governed by the Cloud Native Computing Foundation (CNCF) as an incubating project since April 2023, it provides enterprise-grade authentication and authorization capabilities through OIDC/OAuth 2.0/SAML SSO, identity brokering, and social logins.
Advantages:
- CNCF ecosystem integration with native Kubernetes Operator support and Prometheus monitoring
- Persistent user sessions in v26 ensure seamless authentication during migrations/restarts
- Multi-site deployment optimizations for global enterprise configurations
- Red Hat downstream support with commercial SLAs available through Red Hat SSO
- Extensible architecture supporting LDAP/Active Directory federation and third-party integrations
Disadvantages:
- Complex clustering requiring Kubernetes/OpenShift operational expertise
- Limited mobile SDKs necessitating third-party libraries like AppAuth
- Community-driven support without guaranteed 24/7 incident response
- Experimental status for emerging features like quantum-resistant cryptography
Use this option if...
- You require CNCF-aligned IAM with Envoy service mesh compatibility
- Your team manages Kubernetes environments via Helm/Operators
- Protocol flexibility (SAML/OIDC hybrid flows) is critical
- You need open-source solutions with enterprise upgrade paths
- Data sovereignty and multi-cloud deployments are priorities
- You don't need enterprise level support
10. Roll your own - a solution looking for a problem :-)
It is entirely possible to create a users table and a roles table in your database and create and manage users yourself.
Advantages:
- Developers feel like they're ninjas for a little while
- Can be a quick and dirty solution to the absolute most basic situation
Disadvantages:
-
You have to "reinvent the wheel"
- Identity
- Roles
- Email verification
- Login/Signup/Password reset
- Claims management
- Significant risk
- High maintenance overhead
- Masses of technical debt
Use this option if...
- You want a side project to learn more about how you might roll your own, but of course, you never intend to put it into production :-)
Sample decision - External Applications
External applications are B2B or B2C applications that are intended for consumption outside of your organization.
Example template to customer
Scenario:
- Scope - You are building a consumer facing service that will have multiple clients, including a SPA and a mobile app.
- Social - You want to allow your users to sign up with their social identities (Google, Facebook, Twitter, etc.) but want to allow them to create an account with you if they don't have a social login or don't want to use it.
- All users will have the same level of access once logged in.
- Volume - You anticipate 20,000 active users.
- MFA - You would like to allow users to enable MFA.
Your choices:
- Option A (Recommended) - Microsoft Entra ID provides all of the functionality you need and provides all required functionality in the free tier.
- Option B - Auth0 - Auth0 will meet most of these requirements, however, your volume of users will exceed the free tier and you don't need the additional functionality of the paid tier.
- Option C - IdentityServer - This would work but adds additional management overhead and complexity. You would also need to manage scaling to cope with your volume of users.
Good example - The chosen solution meets the requirements and is highlighted as per Do you manage up?
Sample decision - Internal Applications
For internal applications (referred to as "intranet applications" by Microsoft), the requirements might be different to externally facing applications. For example, they are more likely to be hosted on-premises (rare these days), or may need to use Windows Integrated Authentication (also rare these days, but provides a wonderful UX).
Example template to customer
Scenario:
- Scope - You have an internal enterprise application, which will support approximately 1,000 users.\
- You already have Active Directory in place and are syncing with an Entra tenant.\
- Your users will need to access this application from anywhere.\
- MFA - As per your company security policy, you must enforce MFA.\
Your choices:
- Option A (Recommended) - Microsoft Entra ID (previously Azure Active Directory) - most of the infrastructure for this is already in place for you, and it already meets all your requirements. We would just need to wire up your application to it.
- Option B - Active Directory - while your users are already in AD, it doesn't give you MFA or access outside your network.
- Option C - Okta - this is a sophisticated option but is also expensive and, for this scenario, doesn't provide any advantages over Microsoft Entra ID.
Good example - The chosen solution meets the requirements without adding unnecessary additional costs
Notes:
- All of the following options assume you are building an ASP.NET Core application, although the commercial options listed here provide libraries for most development languages, frameworks, and platforms.
- The information here is relevant as provided, but consider other factors that may impact your decision too. For example, cost may be a factor and saving money may be more important than the added benefits of higher-cost options. Additionally, your situation may not fit neatly into one of the scenarios we have listed and may span multiple scenarios, in which case you may need to pick the option which caters to the broadest set of requirements (avoid 'mix and match').
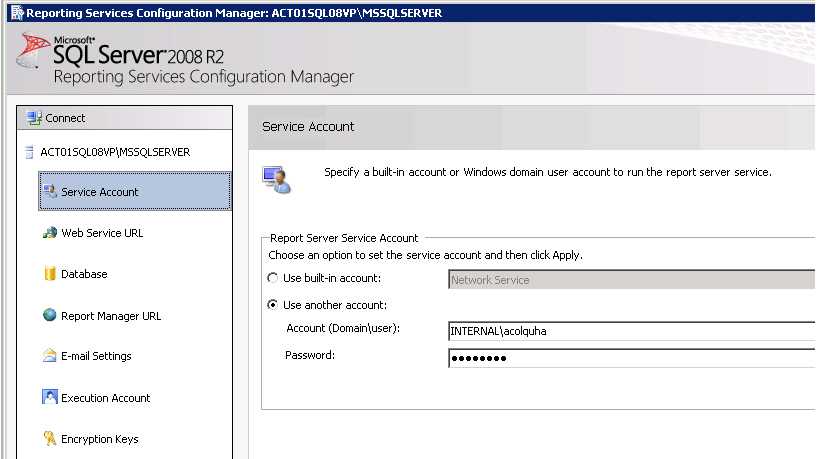
Protecting your Remote Desktop connections is crucial in today's cybersecurity landscape. One effective way to enhance security is by using Azure MFA (Multi-Factor Authentication) in conjunction with the Azure MFA NPS (Network Policy Server) extension. This setup ensures that even if an attacker obtains a user's credentials, they still need a second form of authentication to gain access, significantly reducing the risk of unauthorized access.
Video: Identity Architecture: MFA with RADIUS | Microsoft Entra ID (8 min)Why Use Azure MFA to Protect Servers?
- Enhanced Security: By adding an additional layer of authentication, you mitigate the risk of credential theft.
- Compliance: Many regulatory frameworks require multi-factor authentication to protect sensitive data.
You can follow along Microsoft's documentation to implement this at your company and follow the summary below, if you already fill the prerequisites:
-
Enable the NPS role on a domain-joined server
There needs to be a new server for RADIUS authentication in your environment, solely for MFA prompts. Generally, you don't want MFA for all your RADIUS authentication, so you'll need to create a new one, as it's not possible to have a single server with non-MFA and MFA in it. Once the extension is installed, it's going to analyza every request.
-
Register users for MFA
If users are already registered for MFA in your tenant, then this will work. If not, you need to register them for MFA and ensure it works before proceeding.
-
Install the Azure MFA NPS Extension
This entails running the .exe from Microsoft and running a PowerShell script to connect it to your Azure tenant.
-
Configure your NPS extension
You can configure advanced options at this stage and what happens with users that are not enrolled for MFA.
-
Troubleshoot
If necessary, Microsoft provides scripts and tools to check if your extension is working correctly.You should expect an MFA prompt on your phone every time you connect to a server if this setup was successful.
Finally, implementing Azure MFA for your Remote Desktop connections significantly enhances your security posture. By following the steps above, you can ensure that your remote access solutions are protected against unauthorized access, providing peace of mind and compliance with industry standards.
Do you know who is entering your premises, when, and how? Keys or key-cards can be expensive, they can be lost, and people can loan them to one another without any restriction.
There are all kinds of ways to monitor access to your building and more secure areas. While fingerprint scanners are a good way of monitoring and restricting access, they are difficult to use in practice. Not everyone has great fingerprints, and access can be sketchy and frustrating when it doesn't work.
The best way to do control your Smart Office and Smart Home access is to use an automated NFC (an acronym for Near Field Communication) Access System like Unifi by Ubiquiti.
- You only need your mobile phone, so there are no keys to lose or replace
- It is easy to add or remove access for staff and visitors
- You can see who is coming and going and when
- It can connect to your security cameras for additional security
To see more about how the system works, watch this video from Ubiquiti UniFi Access:
As developers when we think security we commonly become fixated with issues in the code, out of date software versions or incorrectly configured firewalls. However, we miss one glaring vulnerability which there is no patch for: Users.
Social engineering is a technique which mixes art and science to exploit common human behaviours to compromise information systems. The following is a classic example of social engineering performed over the phone.
Video: Live hack and social engineering at DEF_CON by Dave Kennedy and Kevin Mitnick (10 min)There are numerous examples of social engineering ranging from phone calls, attackers posing as friends on social media, all the way to sophisticated attempts at phishing users with near-perfect clones of popular websites.
Figure: ‘Do you think the average consumer could spot the phishing site?’ Source: Troy Hunt The only solution to social engineering is to train properly and prepare users about the dangers presented by and common techniques used by malicious individuals.
For useful information on the topic reference the document ‘Avoiding Social Engineering and Phishing Attacks’ by the United States Computer Emergency Readiness Team or the Pluralsight course Ethical Hacking: Social Engineering by Troy Hunt.
With the above in mind, it is important to review regularly the information availed via search engines and standard operating procedures. Furthermore, it can be useful to test the readiness and alertness of staff by performing mock social engineering attacks.
Take the following situation as an example: the CEO is out of town and decides to use an employee’s laptop left in the office on the weekend, the employee in question is messaged via Skype for their domain password. If the employee is aware of the risks, this poses the company then they would not send the requested credentials and follow proper procedure around reporting a suspected incident.
The following checklist is a good example of areas to focus on:
- Run penetration tests with SSLLabs.com to check how exposed your servers are
- Look for passwords in .config and code (SSW Code Auditor can help)
- Authentication process of identifying who the user is
- Authorization what the user can do within the application
- Licensing to control the usage of the software
- Validation of all inputs in the system (cross site scripting (XSS) and SQL injection)
- No in memory generation of SQL statements (and are they using a good ORM)
- Encryption of passwords and any sensitive data
- Software Licensing protection mechanisms (and a recommendation to a subscription model)
- Methodologies and best practices to reduce your exposure to hostile attacks
- Logging who is doing what and when (audit trails)
There is a more comprehensive list here on GitHub: A practical security guide for web developers.
Did you know that you can stop your users from logging into any of your Azure or Office365 resources based on the location they are in? What about the types of devices that they can connect from or only allowing connections that use MFA? These things are all possible to restrict.
This seriously limits the attack surface and also helps to stop compromised devices and accounts from being used.
Configure locations
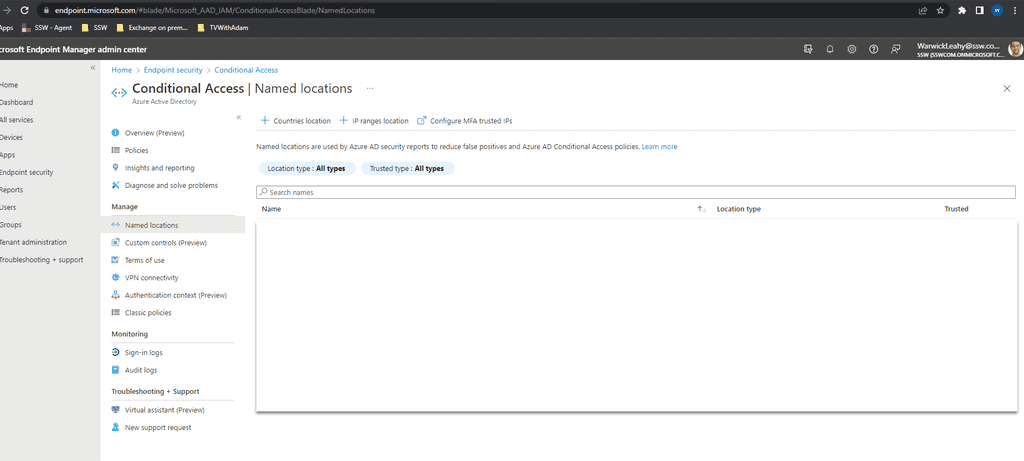
First you need to add any locations that you require for your office.
- Go to https://endpoint.microsoft.com | Endpoint security | Conditional Access | Named locations
-
Click + Countries location and add required countries
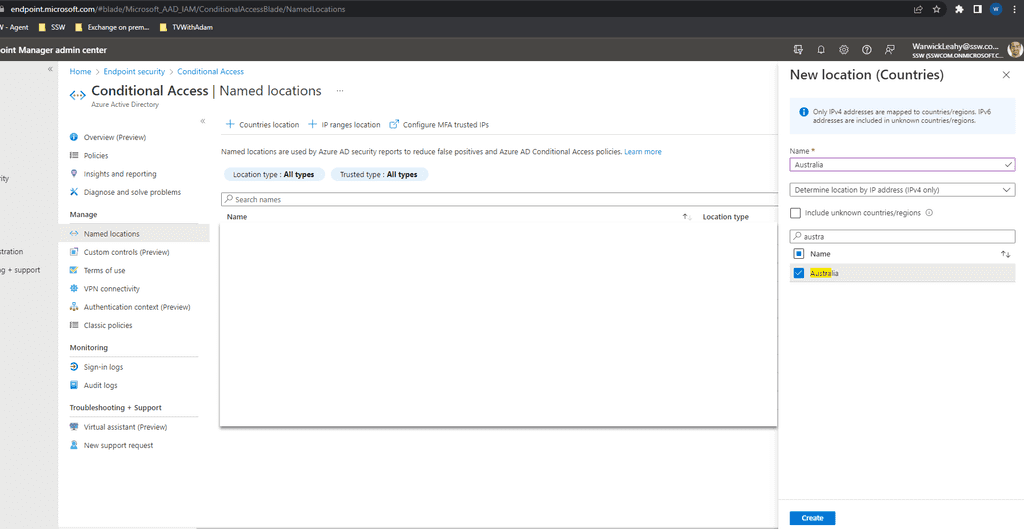
Figure: Add a location -
Add as many as you require for your users to access
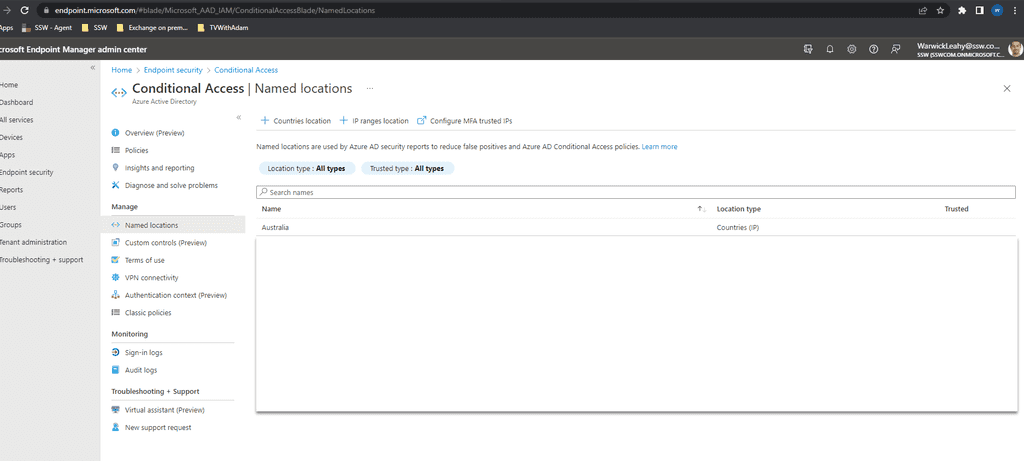
Figure: Every location that your users work from
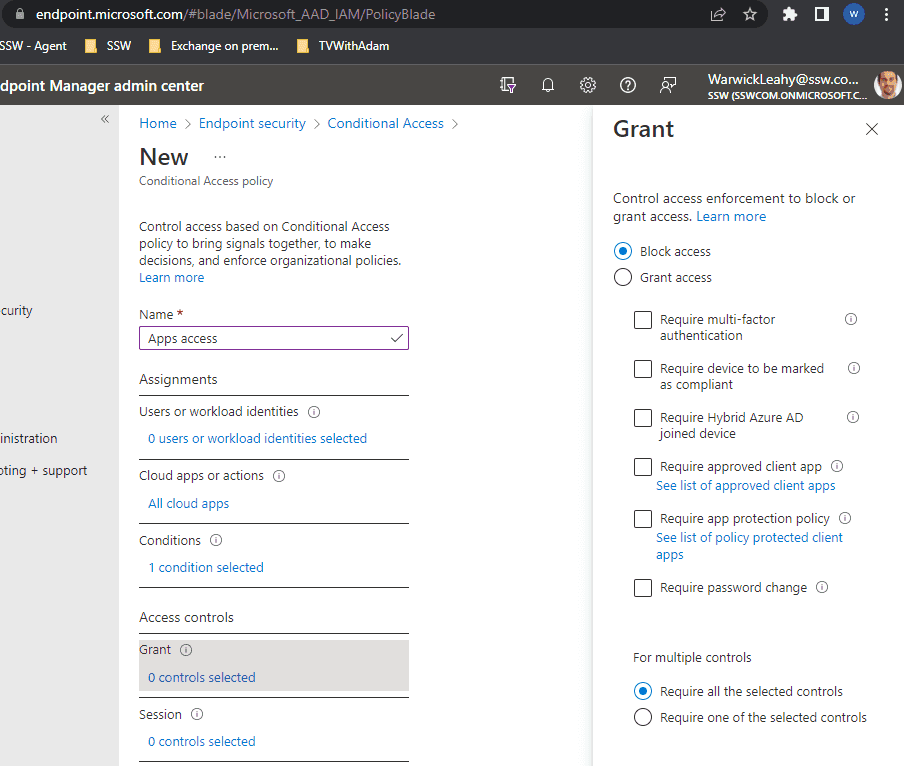
Configure policies
Now configure some policies to implement these rules
- Go to https://endpoint.microsoft.com | Endpoint security | Conditional Access | Policies
-
Select New policy | Create new policy
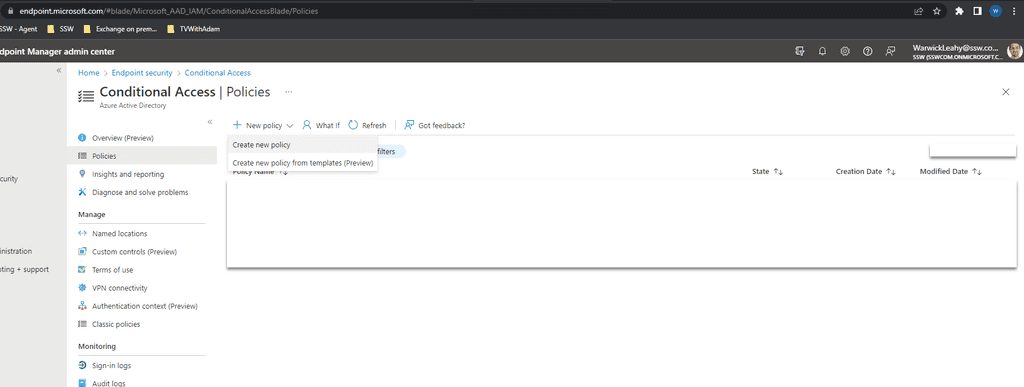
Figure: Add a conditional access policy -
Give it a name then select Cloud apps or actions | Select All cloud apps
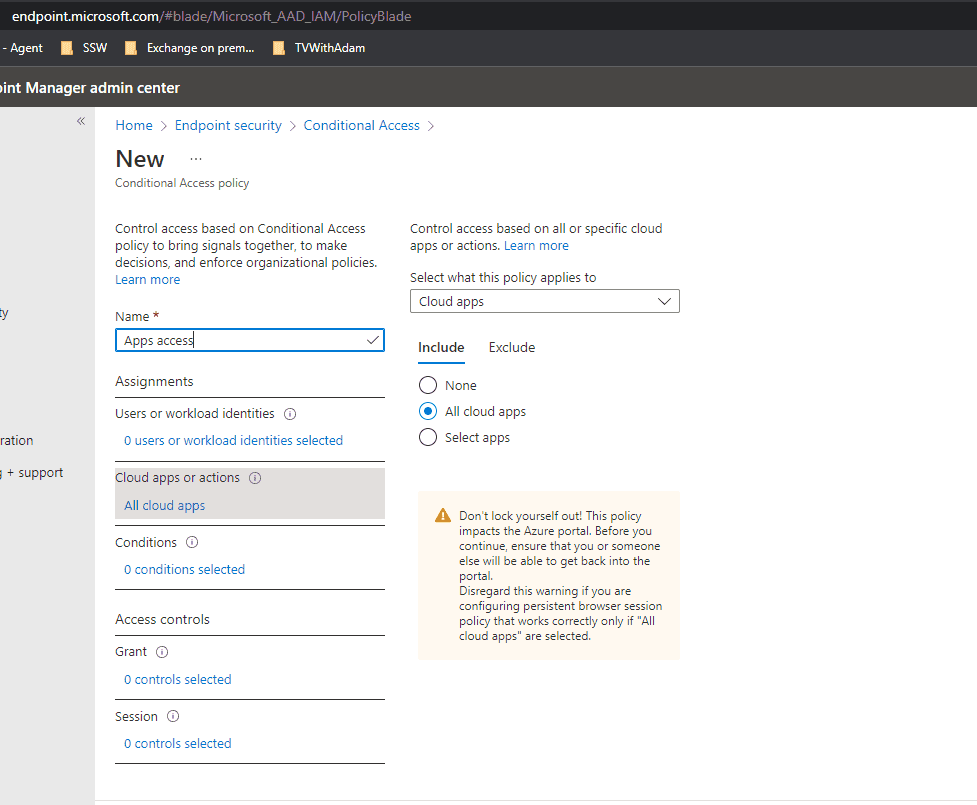
Figure: Add all cloud apps -
Select Conditions | Locations Then set configure to yes and Include to "Any location"
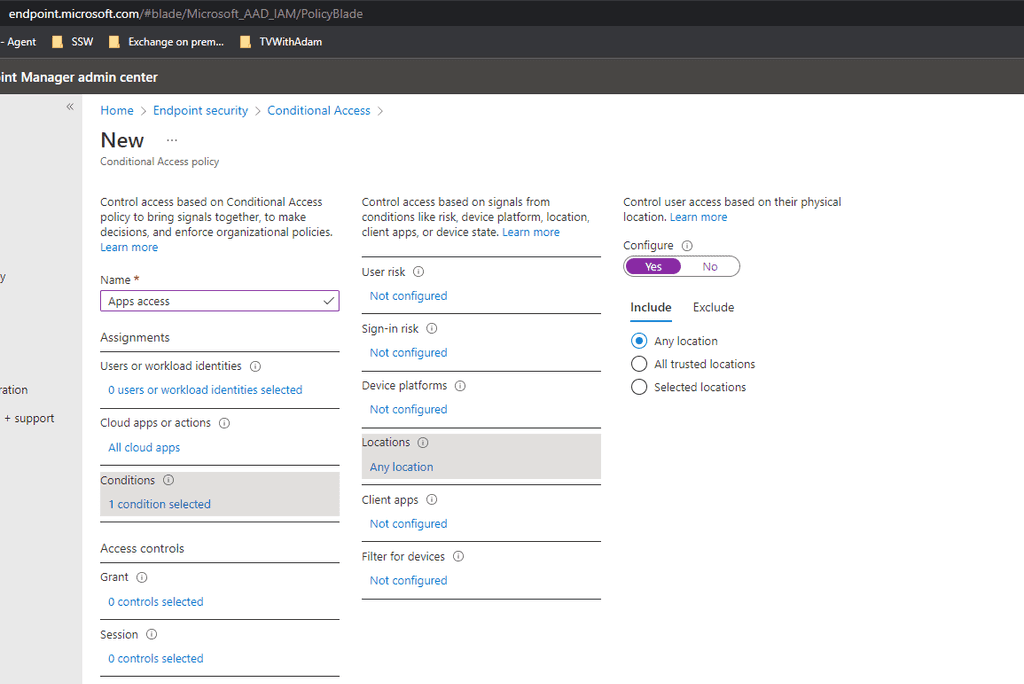
Figure: Choose any location -
On Exclude choose Selected locations and then exclude your workers countries (i.e. Australia)
Note: This must be done this way as the user must not meet a block access rule ever if they are to login.
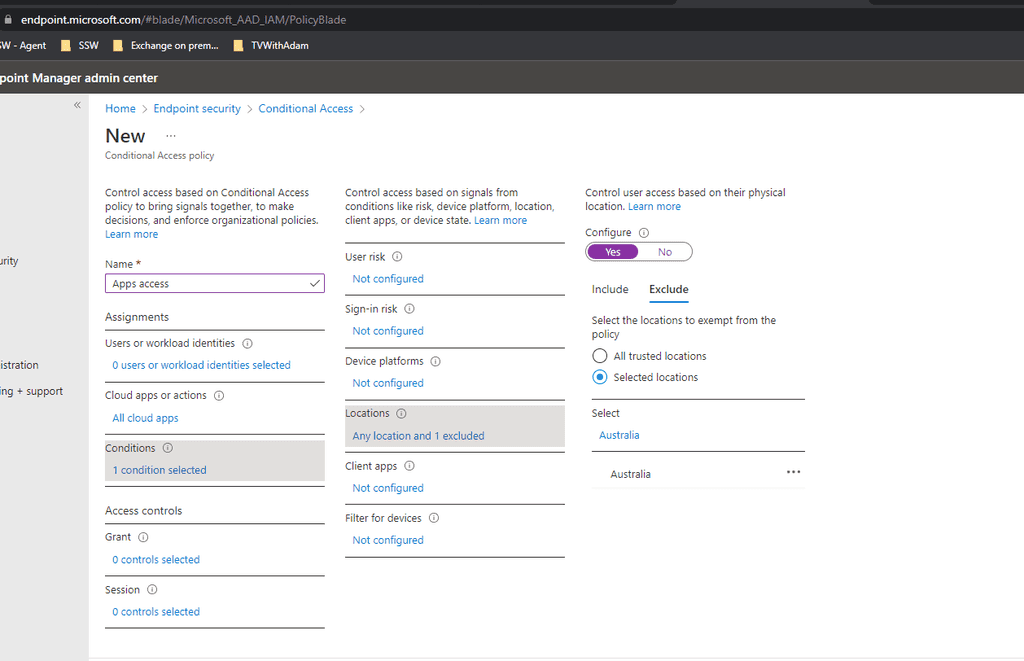
Figure: Exclude good locations Create a grant rule
- Similarly create a rule that applies to all cloud apps as above
-
This will be exactly the same as the above rule except that you should not have conditions and should Grant access with MFA
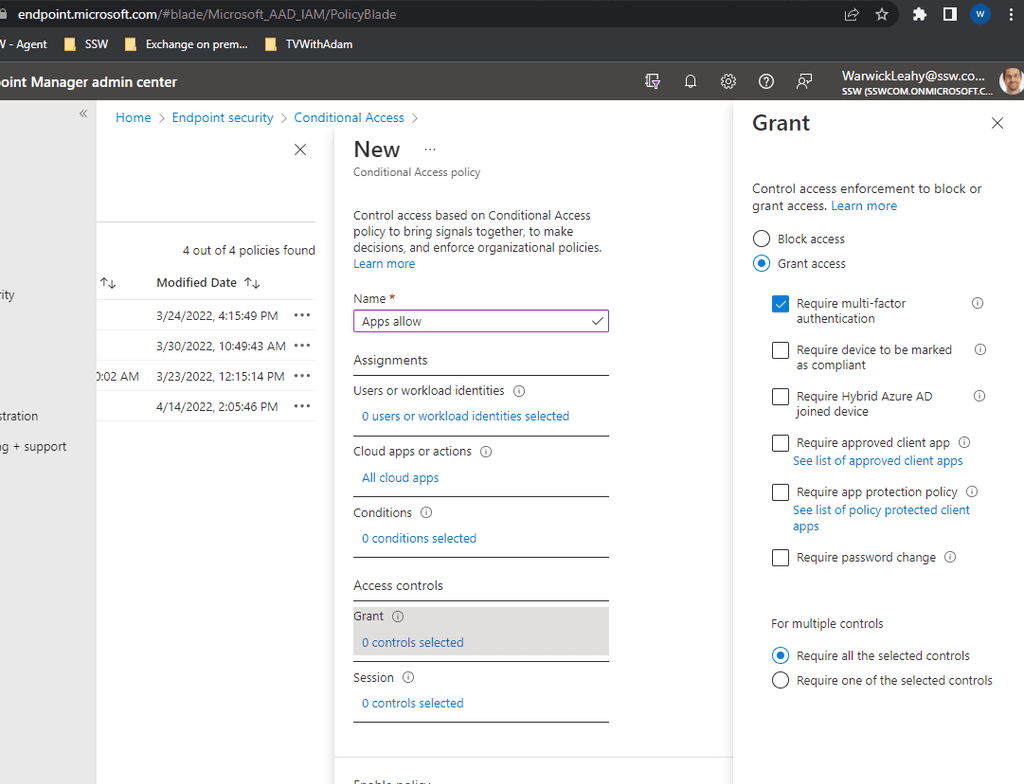
Figure: Add a grant with MFA -
You will notice that each of these rules have a 'Report only' mode or enforce. You should leave it on report mode and monitor the audit logs.
Check for any failures and only apply the rules to a small subset of your users before changing them to 'On'. This is very important as you can stop everyone including yourself from logging in.
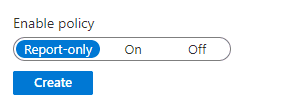
Figure: Choose report only until you are sure that your rules work
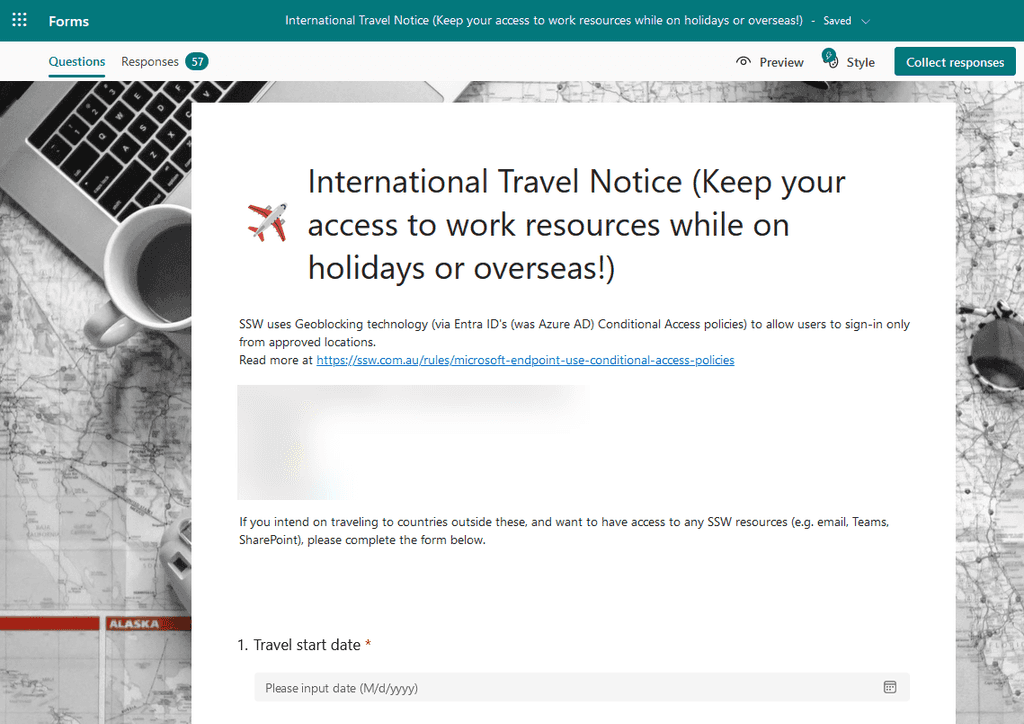
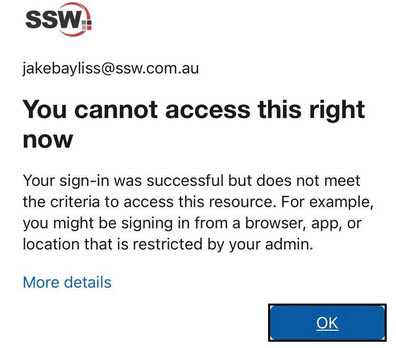
International Travel Notice - Exclude travelling users and let them keep their access to work resources while on holidays or overseas
When a user goes overseas and needs access to the company resources, you should temporarily exclude them from the Block Access policy.
Traveling users should inform and request access prior to their departure. A good way to do this is via Microsoft Forms:
Otherwise they will get this message:
Microsoft Defender XDR is an enterprise endpoint security platform designed to help enterprise networks prevent, detect, investigate, and respond to advanced threats. It is managed at https://security.microsoft.com/
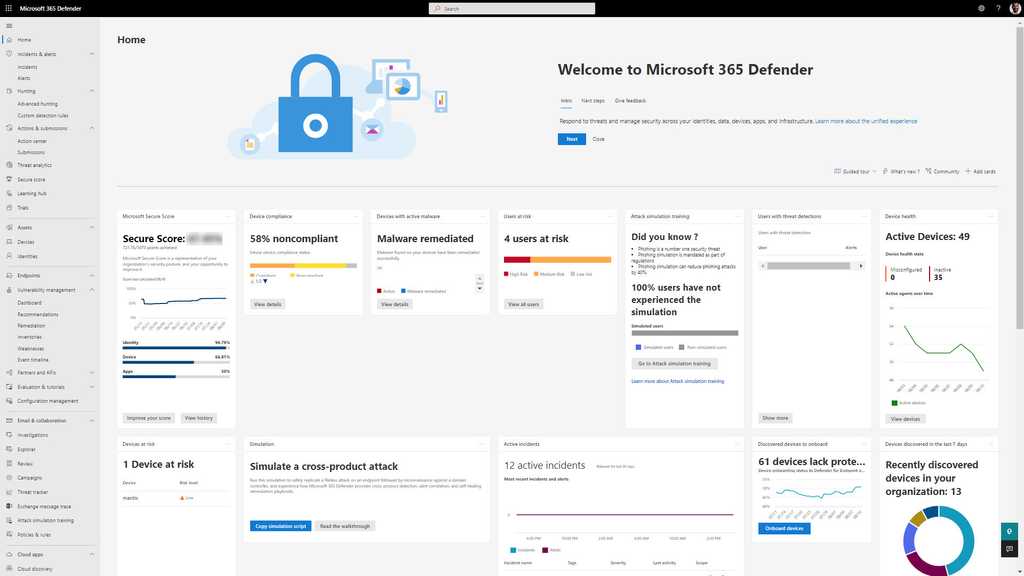
Figure: Microsoft Defender XDR – Dashboard There are a number of licensing options - check out Microsoft's documentation for information.
Configuration
Follow the instructions to install Defender on Workstations:
Follow the instructions to install Defender on Servers:
- Defender for Endpoint: Onboard servers
-
Defender for Identity: Onboard domain controllers
- The Azure Advanced Threat Protection sensor configurations vary depending on whether Endpoint or Identity is installed.
Secure Score
Microsoft Secure Score is a measurement of an organization's security posture, based on data from Defender for Endpoint and other Microsoft security products. It can be found at security.microsoft.com/securescore.
Points are given as per the following actions:
- Configuring recommended security features
- Remediating vulnerabilities
- Addressing the improvement action with a third-party application or software, or an alternate mitigation
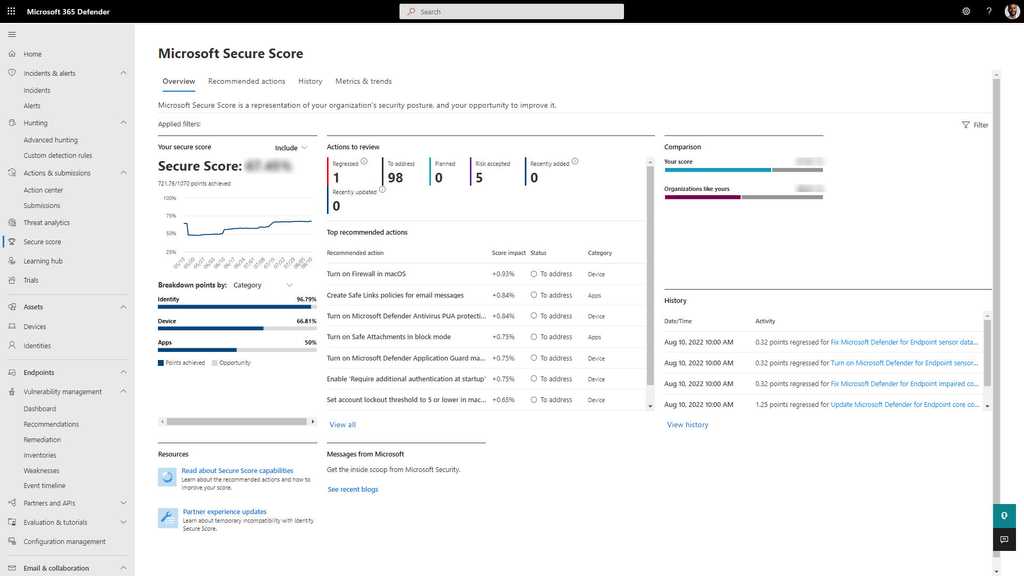
Figure: Microsoft Secure Score How to increase Secure Score
Each improvement activity is worth up to 10 points, based on their importance. Points are obtained by implementing security recommendations, such as updating software or configuring Intune policies (or GPOs) to secure user accounts and devices.
Security admins should check this score regularly and improve the score where possible.
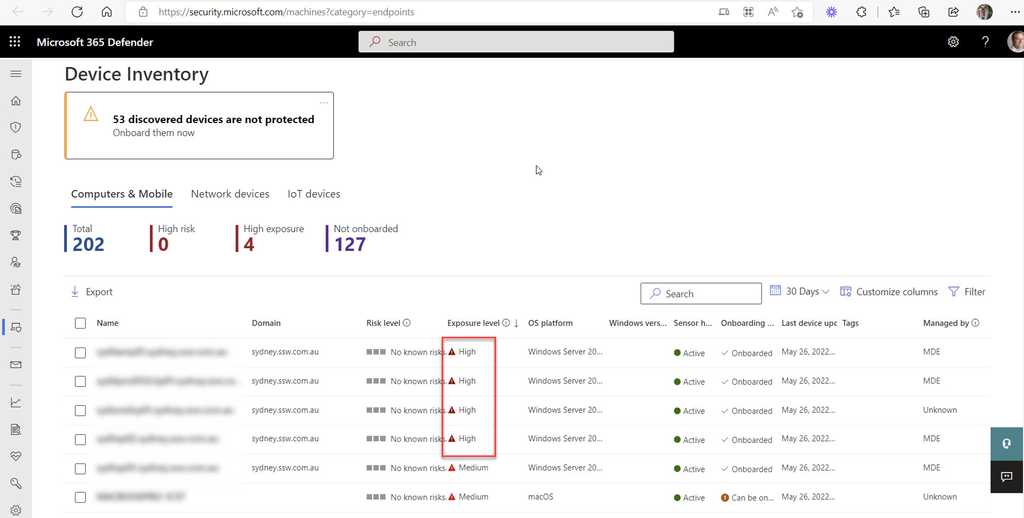
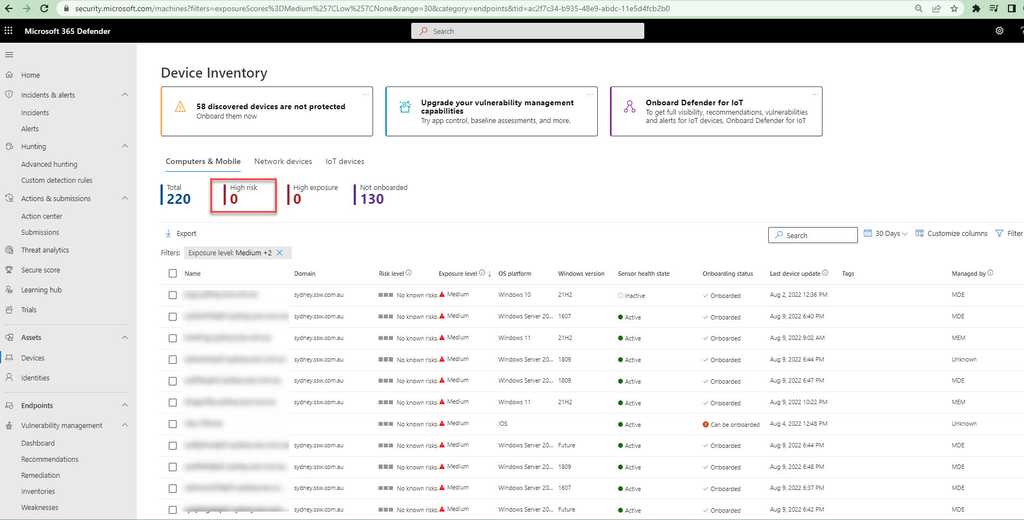
Device Inventory
Device inventory shows a list of the devices in your network. Devices are added to the device inventory through the Microsoft Defender for the Endpoint onboarding process. You’ll see information such as device name, domain, risk level, exposure level, OS platform, onboarding status, sensor health state, and other details for easy identification of devices most at risk.
Risk level reflects the overall risk assessment of the device based on combination of factors, including the types and severity of active alerts on the device. Resolving active alerts, approving remediation activities, and suppressing subsequent alerts can lower the risk level.
Exposure level reflects the current exposure of this device based on the cumulative impact of its pending security recommendations.
Security admins should check this page regularly and reduce the risk/exposure/criticality levels where possible.
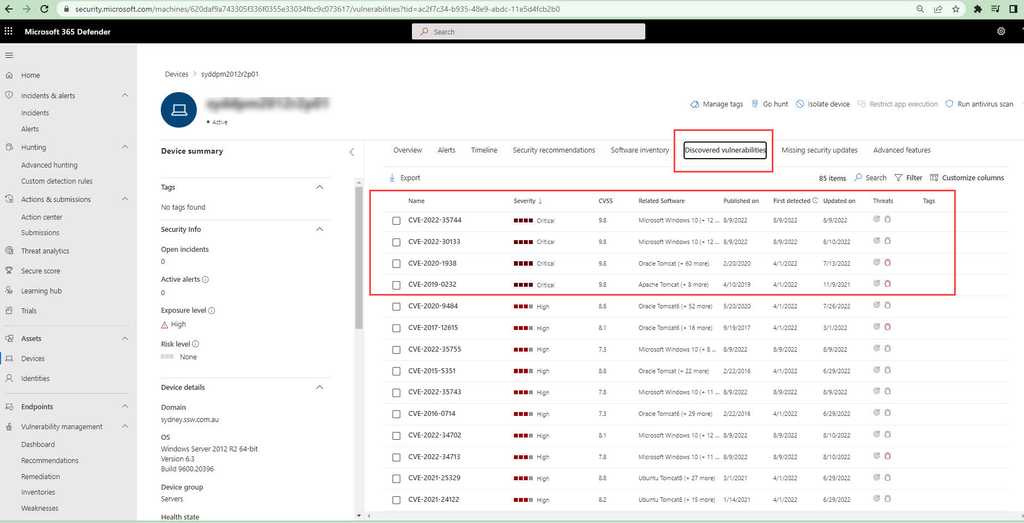
Figure: Severity level – High Exposure Security Recommendations
The Microsoft Defender portal has security recommendations for exposed devices which can be remediated manually after doing the needful (maybe a simple update): https://security.microsoft.com/security-recommendations/
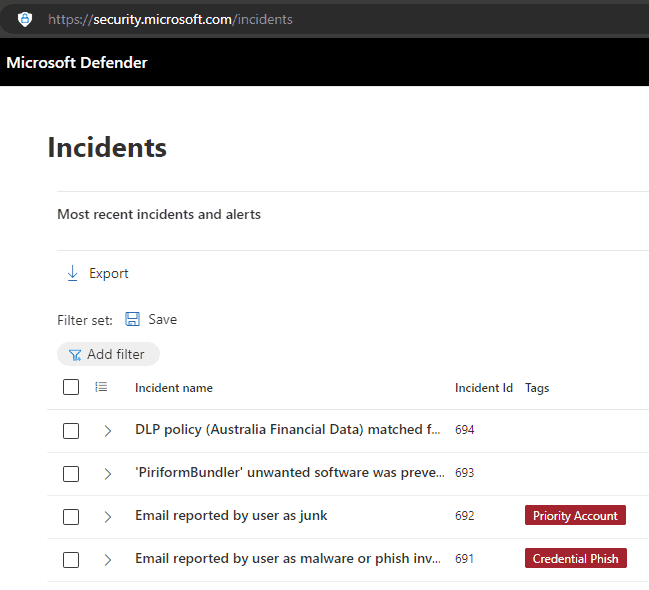
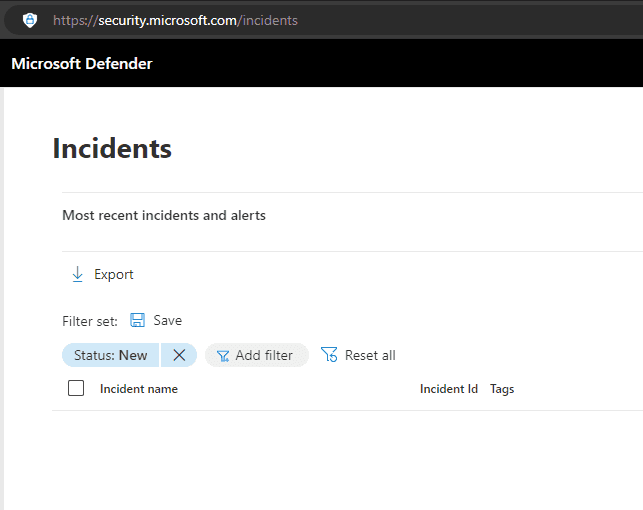
Incidents & Alerts
In Microsoft Defender XDR, an incident is a collection of correlated alerts and associated data that define the complete story of an attack. Defender for Office 365 alerts, automated investigation and response (AIR), and the outcome of the investigations are natively integrated and correlated on the Incidents page.
When critical incidents occur, you should receive an email notification so that you can act on the alert immediately.
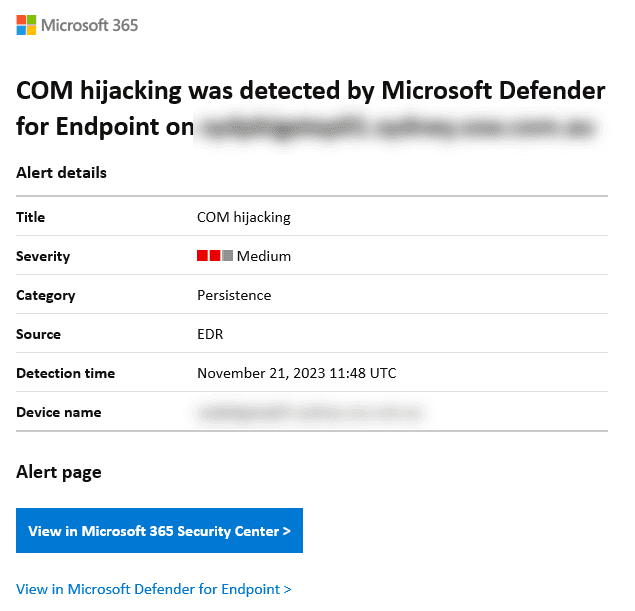
Figure: Example email alert from Defender However, it is also important to check the Incidents page in Defender, to resolve less critical alerts - or email alerts that you may have missed. It is a good idea to set a reminder to check this page weekly.
These alerts can include emails that have been reported as malware or phishing, data loss prevention (DLP), or unwanted software detections.
In today's complex digital landscape, managing user access to resources can be a daunting task for organizations. Entra Access Packages emerge as a game-changer in this scenario, offering a streamlined and efficient approach to identity and access management.
By bundling related resources into cohesive packages, they simplify the process of granting, reviewing, and revoking access. This not only reduces administrative overhead but also enhances security by ensuring that users have the right permissions at the right time. Furthermore, with built-in automation features like approval workflows and periodic access reviews, organizations can maintain a robust and compliant access governance structure. Adopting Azure Access Packages is a strategic move for businesses aiming to strike a balance between operational efficiency and stringent security.
❌ Bad Example - Manually Requesting Access via Email
In the old-fashioned way, users would send an email to the SysAdmins requesting access to a specific resource. This method is prone to errors, lacks an audit trail, and can lead to security vulnerabilities.
To: SysAdmins Cc: Subject: Request for Access to SugarLearning Prod Figure: Bad example - This requires manual changes by a SysAdmin
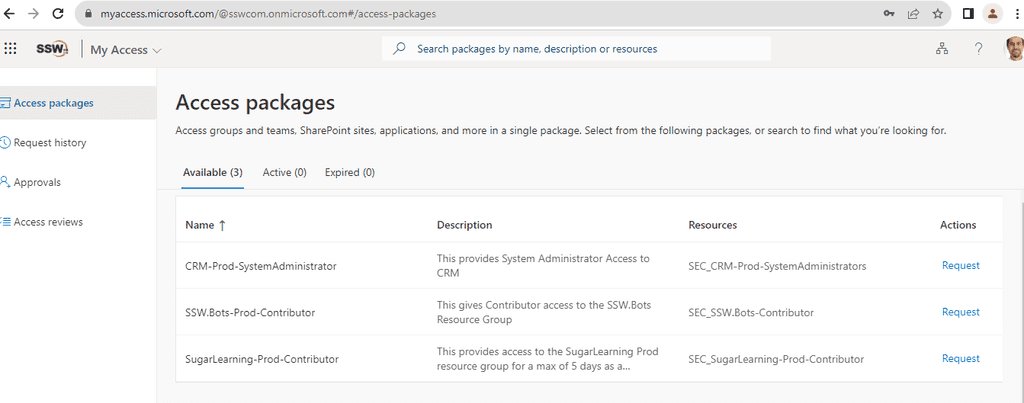
✅ Good Example - Requesting Access via myaccess.microsoft.com
Instead of manually sending emails, users can request access through
myaccess.microsoft.com, which provides a streamlined, auditable, and secure method.-
Navigate to
myaccess.microsoft.com -
Search for the desired resource or access package.
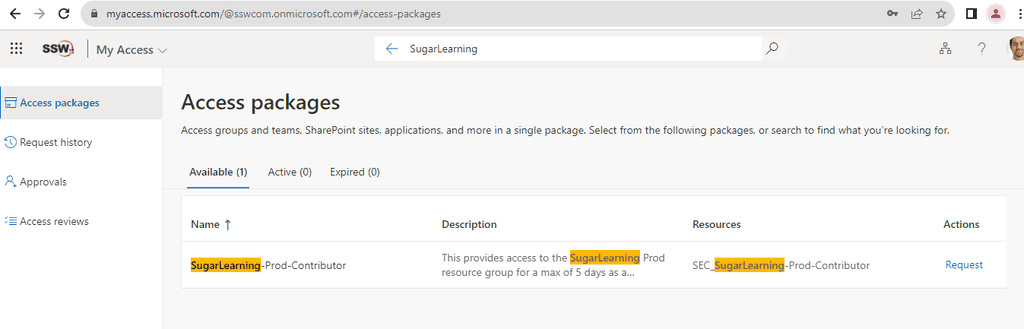
Figure: Search for the required resource -
Request Access by selecting the appropriate access package and filling out any necessary details.
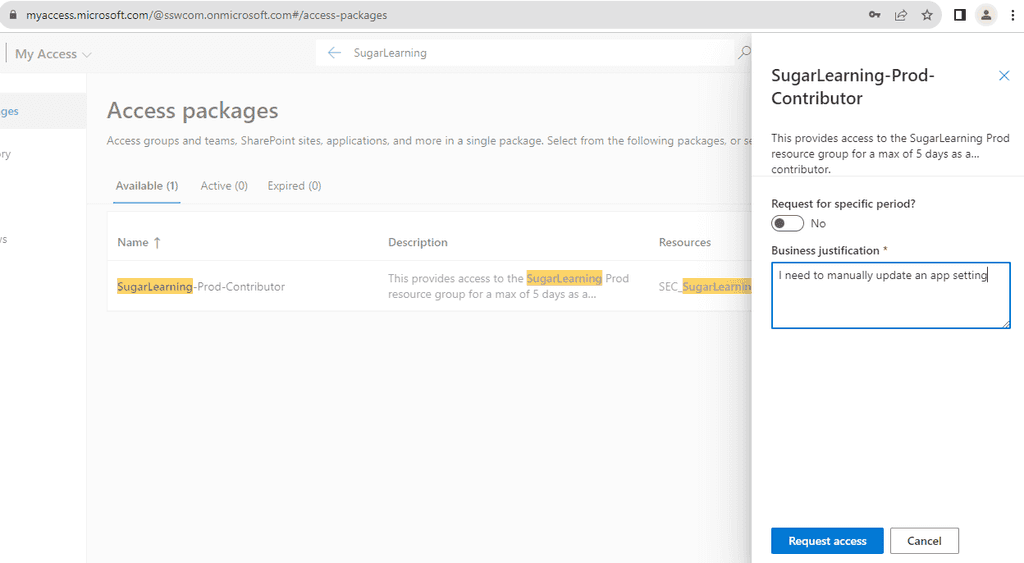
Request Access -
Wait for approval from the people responsible for the resource
If you require immediate access ping them on Teams
Steps to Create an Access Package
-
Open Azure Portal: Navigate to Entra ID | Identity Governance | Access packages.
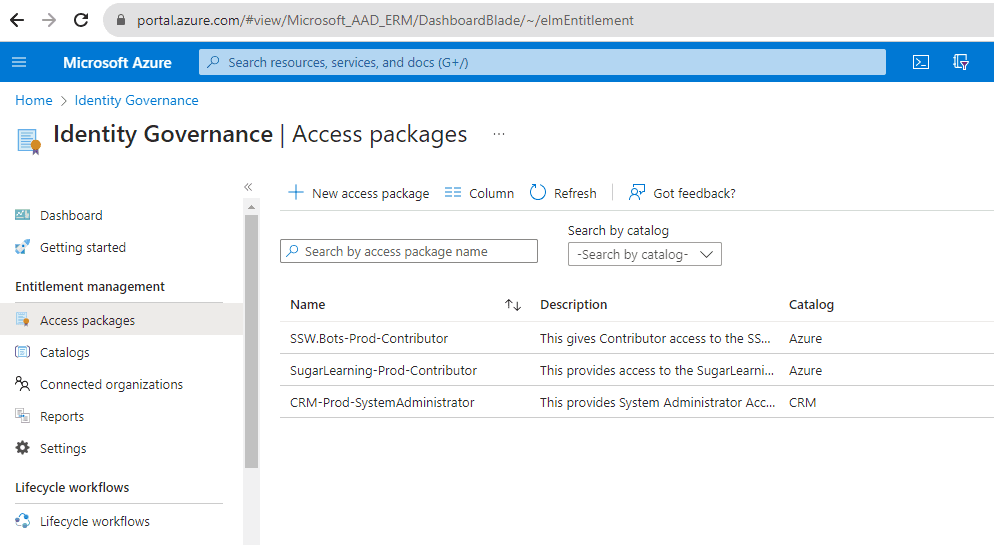
Figure: Navigate to Azure portal | Access packages | New Access package - New Access Package: Click on
+ New access package. -
Fill Details: Provide a name, description, and select the catalog for the access package.
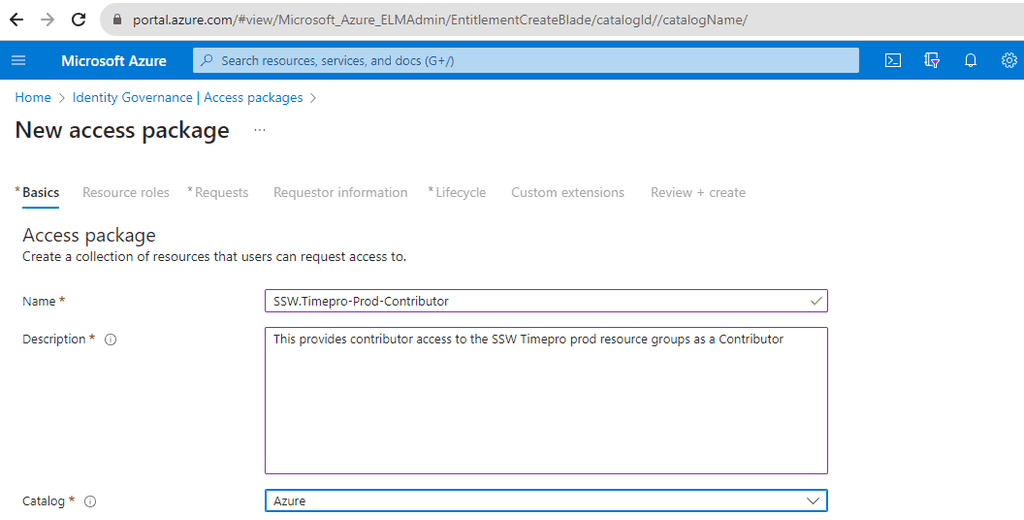
Figure: Fill out the details and choose a catalog -
Define Resources: Add the resources (applications, groups, SharePoint sites) that users will get access to when they request this package.
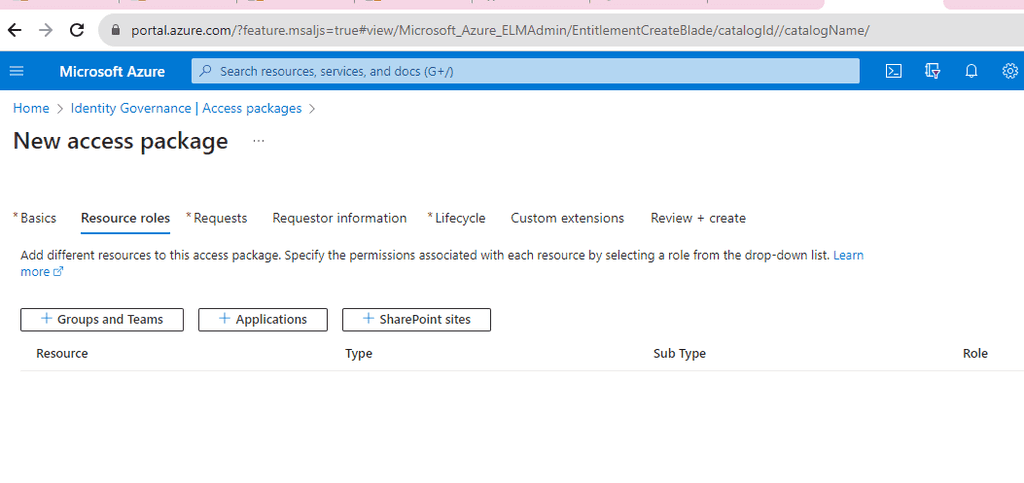
Figure: Add the required resources -
Set Policies: Define who can request the package, approval workflows, duration of access, and other settings.
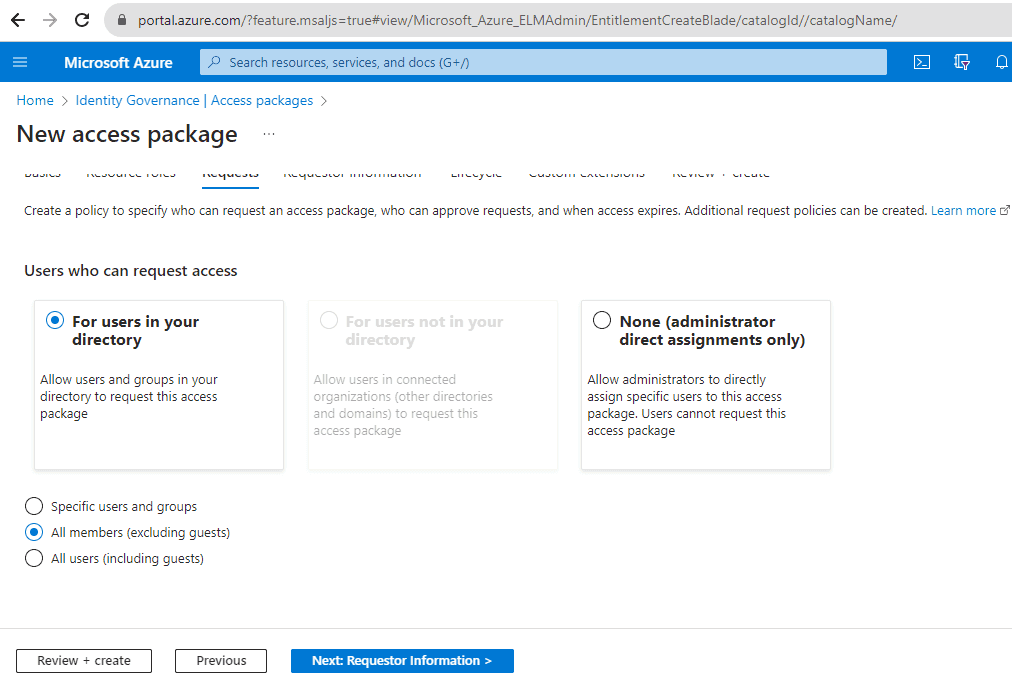
Figure: Choose the types of users that can request access 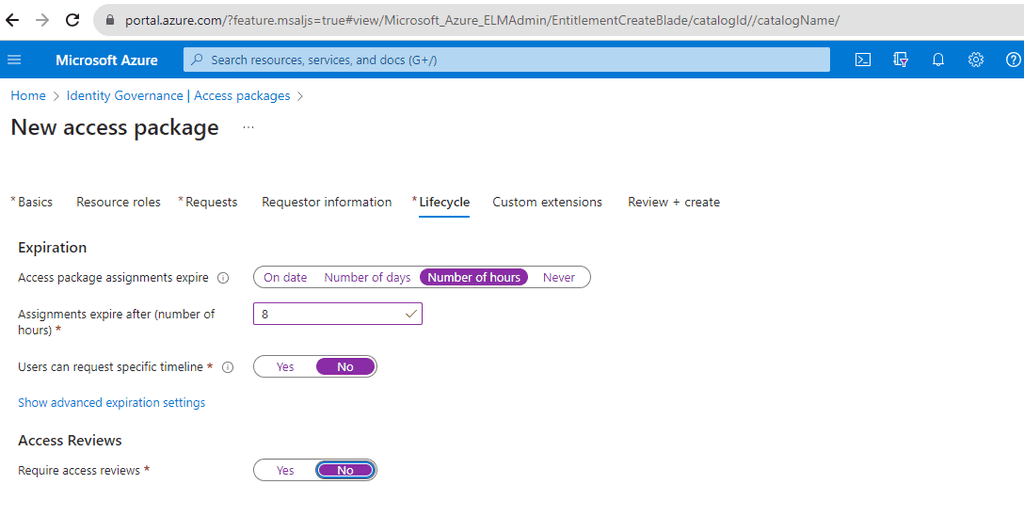
Figure: Choose policies that match the level of access -
Review and Create: Ensure all details are correct and then create the access package.
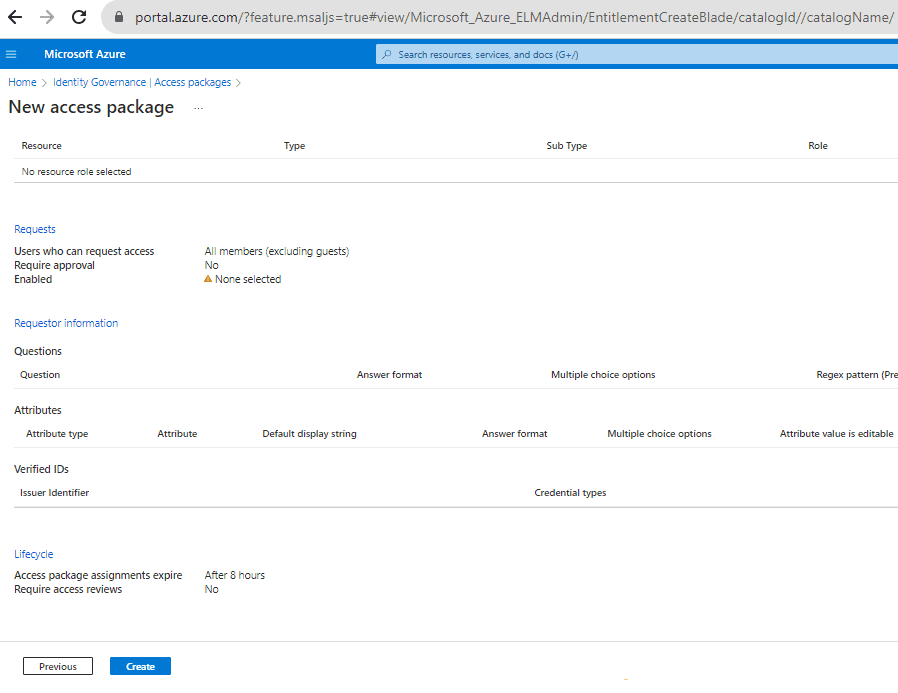
Figure: Review the settings and create the policy
-
Leveraging SCIM (System for Cross-domain Identity Management) in conjunction with Entra ID (or whatever Identity provider you use) is crucial for efficient and secure identity synchronization across cloud-based applications and services.
Why Integrate SCIM with Entra ID?
Integrating SCIM with Entra ID automates the process of managing user identities in cloud applications. This integration streamlines user creation, modification, and deletion, reducing manual errors, saving administrative time, and enhancing security.
Bad Example
Relying solely on manual identity management processes in Entra ID without SCIM integration. This manual approach is inefficient, prone to errors, and can lead to security risks due to inconsistent identity data across applications.
Good Example
Implementing SCIM to automate user provisioning and deprovisioning across various cloud services. This ensures consistent identity data, improves security, and reduces the administrative burden.
By integrating SCIM with Entra ID, organizations can achieve a more streamlined, secure, and efficient approach to identity management across their cloud ecosystem.
Intune is a feature that focuses on mobile device management (MDM) and mobile application management (MAM). You control how your organization’s devices are used, including mobile phones, tablets, and laptops. You can also configure specific policies to control applications.
Intune is a part of Microsoft's Enterprise Mobility + Security (EMS) suite. It integrates with Entra ID to control who has access and what they can access.
With Intune, you can:
- Choose to be 100% cloud with Intune, or be co-managed with Configuration Manager and Intune
- Set rules and configure settings on personal and organization-owned devices to access data and networks
- Deploy and authenticate apps on devices - on-premises and mobile
- Protect your company information by controlling the way users access and share information
- Be sure devices and apps are compliant with your security requirements
Managing Devices
When Intune is connected to Entra ID its automatic enrollment lets users enroll their Windows devices in Intune. To enroll, users add their work account to their personally owned devices or join corporate-owned devices to Entra ID.
If you are using Conditional Access for MFA, you will need to add an exception for the Microsoft Intune Enrollment app for hybrid-joined devices to be able to enroll.
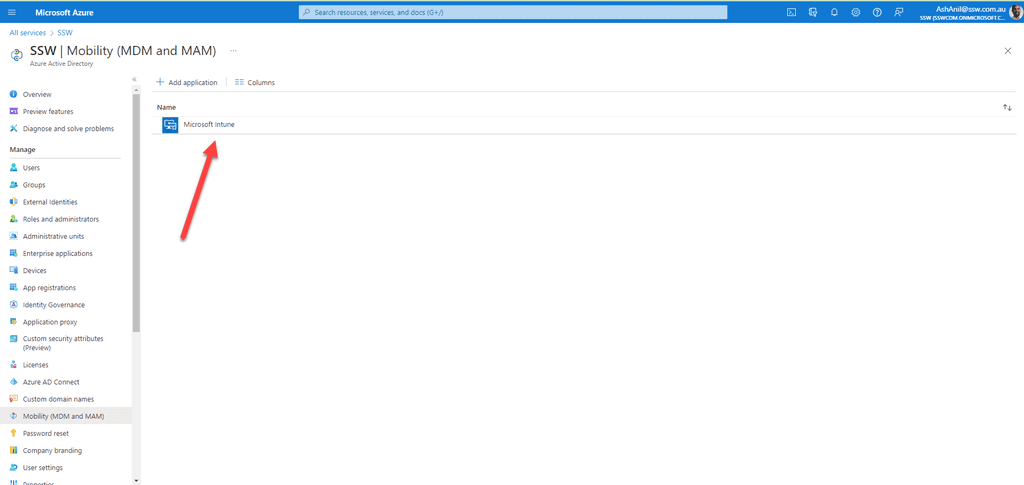
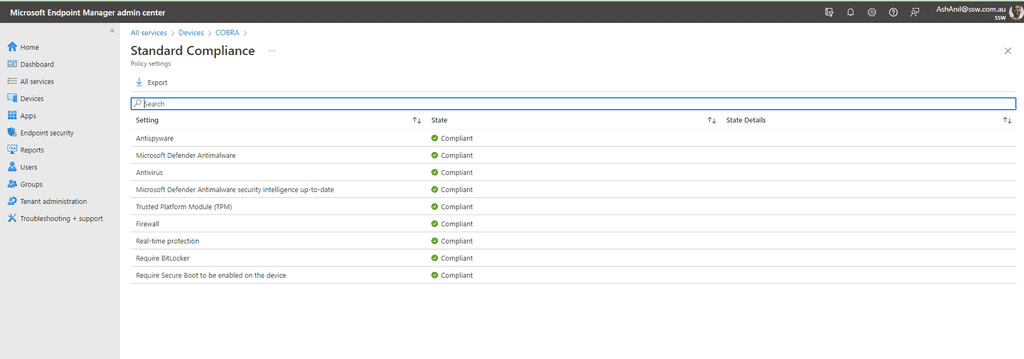
Figure: Intune connected to Entra ID - SysAdmins can monitor all the windows devices from Microsoft Endpoint Manager admin center
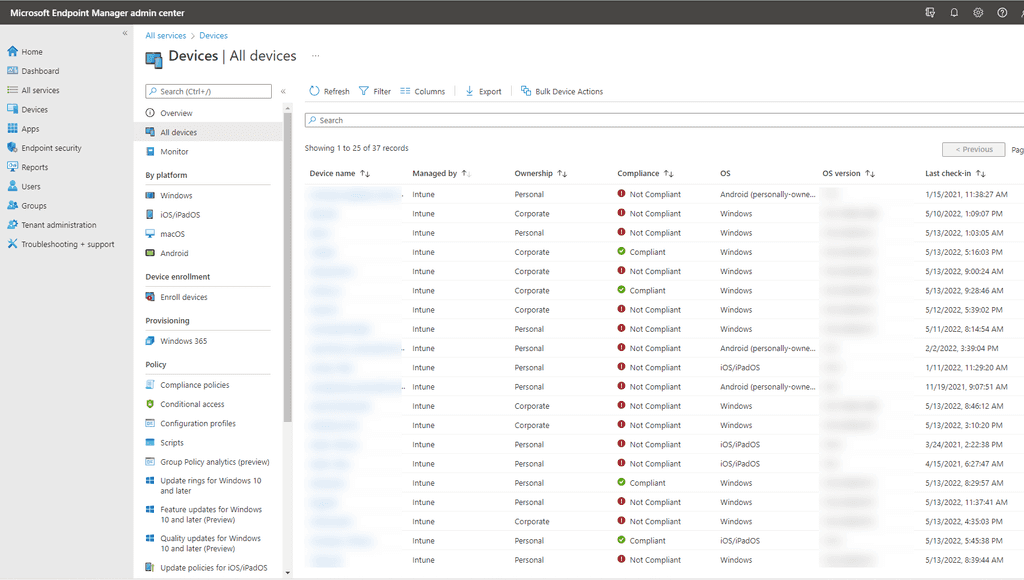
Figure: Devices managed by Intune - We can get reports on device compliance at any time.
There are many other MDM solutions out there, but Intune is best if you're mostly managing Windows devices (and some iOS/Android as well). JAMF is a great option if you're only using iOS/MacOS devices.
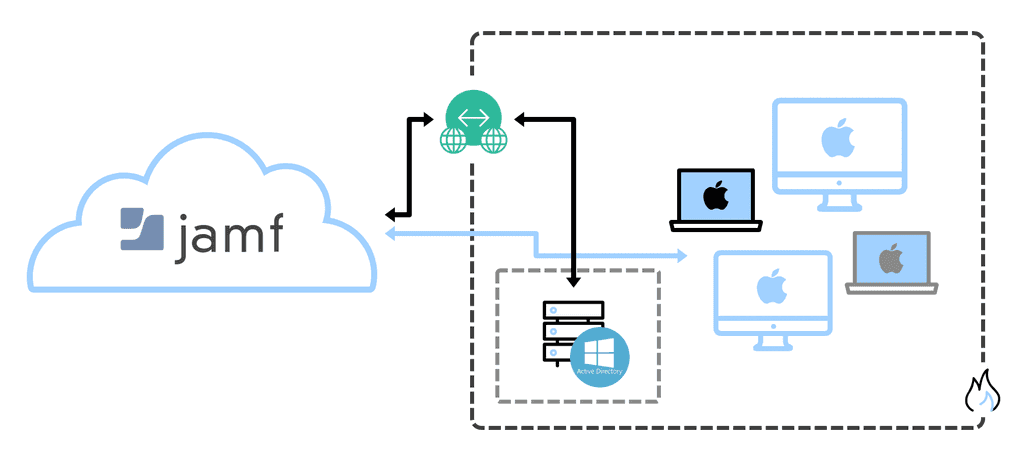
Figure: Jamf architecture to monitor IOS devices Ensuring the security of personal data is paramount. However, when breaches occur, it's essential to approach them with understanding and support. This not only fosters trust among staff but also provides valuable insights for proactive security measures.
Benefits of having an open policy for personal data breaches
- Building Trust - An open policy assures staff that they will receive assistance without punitive repercussions. This encourages them to report breaches promptly
- Enhanced Monitoring - By being informed of breaches, the security team can intensify user activity monitoring in the subsequent weeks
- Proactive Identification - With increased monitoring, suspicious behaviors can be detected and addressed before they escalate into significant breaches
How to implement and manage personal data breaches
- Training - Regularly train end-users on the importance of data security and the procedures to follow in case of a breach
- Open Communication - Encourage staff to report any potential breaches without fear of punitive actions
- Active Monitoring - Once a breach is reported, increase the monitoring of the involved user's activity to detect any unusual patterns
By adopting an open policy, organizations can turn potential security threats into opportunities for strengthening their defenses and building a culture of trust.
When using IdentityServer 5 (aka Duende IdentityServer), you don't need to use
UseDeveloperSigningCredentials()anymore as it is now enabled by default.services.AddIdentityServer() .AddInMemoryClients(new List<Client>()) .AddInMemoryIdentityResources(new List<IdentityResource>()) .AddInMemoryApiResources(new List<ApiResource>()) .AddInMemoryApiScopes(new List<ApiScope>()) .AddTestUsers(new List<TestUser>()) .AddDeveloperSigningCredential();Figure: Bad example - you don't need to use
.AddDevelopersSigningCredential()anymoreWhen using version 5, instead of using
IdentityServer4.AccessTokenValidation(), you should use the out of the boxAddAuthentication(("Bearer").AddJwtBearer("Bearer")from .NET 5services.AddAuthentication("Bearer") .AddIdentityServerAuthentication("Bearer", options => { options.ApiName = "api1"; options.Authority = "https://localhost:5000"; });Figure: Bad example - don't use
IdentityServer4.AccessTokenValidationpackage as it is deprecated.services.AddAuthentication("Bearer") .AddJwtBearer("Bearer", options => { options.Audience = "api1"; options.Authority = "https://localhost:5000"; });Figure: Good example - use
AddJwtBearer("Bearer")insteadWhen hackers or security researchers find a vulnerability in your system, they need a way to tell you. If you don’t have a [email protected] email, they might give up or go public.
Your
security@inbox is your first line of defense.It helps with:
- Responsible disclosure from ethical hackers
- Bug bounty submissions
- Early warnings before public leaks
You don’t need a full bug bounty program to start. Just set up the email, publish it (e.g. in your security.txt), and monitor it.
Make sure it’s:
- Monitored by trusted staff (not just one person)
- Responded to quickly (aim for <48h)
- Part of your incident response process
Bad example: No security@ exists. The researcher tweets the exploit. The company finds out via media. Damage is done.
Good example: A security researcher finds a critical bug and emails security@. The team replies in 1 day, verifies the issue, patches it in a week, and thanks the reporter.
Be aware of "beg bounties" – people who send low-risk reports and demand money. You can politely thank them or ignore if it’s not a real issue.
Want ethical hackers to help you? Add a security.txt file with your security contact information. Check out how we setup ours - https://github.com/SSWConsulting/securitytxt
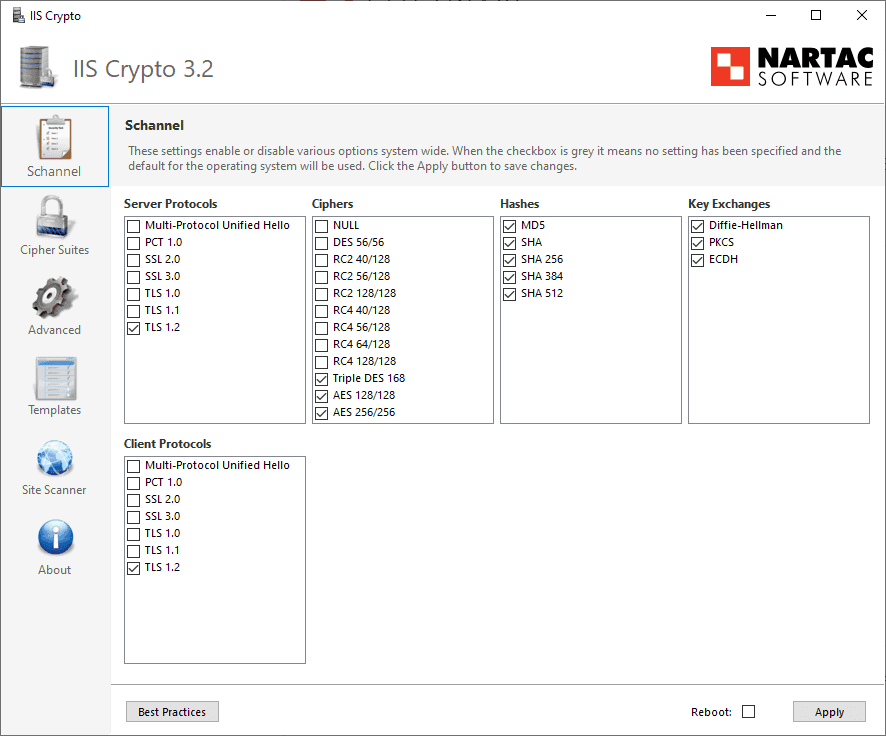
For better server security (especially regarding public facing servers), certain security protocols and ciphers should be disabled.
Using a tool called "IIS Crypto 3.2" by Nartac, these protocols can be easily disabled instead of having to manually edit the Registry Keys.
- Download IIS Crypto 3.2 (https://www.nartac.com/Products/IISCrypto/Download)
- Run this on the server you wish to lock down
- Select the best practices button
- Ensure that TLS 1.0 and TLS 1.1 is also disabled | hit apply
- The server will need to be rebooted before the settings take effect
If you need to remember the password then a passphrase is best. Preferably these should be made up of 4 random words with a length of at least 16 characters. These eliminate the requirement for special characters and are incredibly difficult for a computer to guess.
A strong password would look something like this:
correcthorsebatterystaple
OK example - A strong memorable password
However the best passwords in the world are the ones you can never possibly remember. Computer generated passwords, with a length of at least 16 characters, offer the most protection. A super strong password looks something like this:
$Jun!ZW@gYS%bmy0($34hYj&8hsgfDF
Good example - A strong computer-generated password
This is obviously not something you can realistically type in every time you need to use it. Fortunately, the same tools that generate these for us also manage them, storing them securely and automatically entering them into websites and apps for us.
With a password manager, you don't have to remember that strong, unique password for every website. The password manager stores them for you and even helps you generate new, random ones.
It does not matter which one. There are many great tools out there:
Figure: Why you should use a password manager
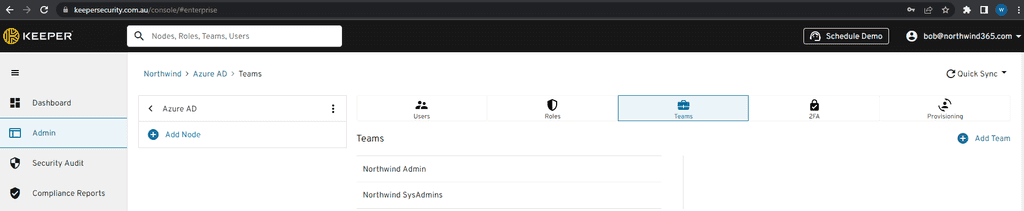
In an Enterprise you should use an Enterprise password manager
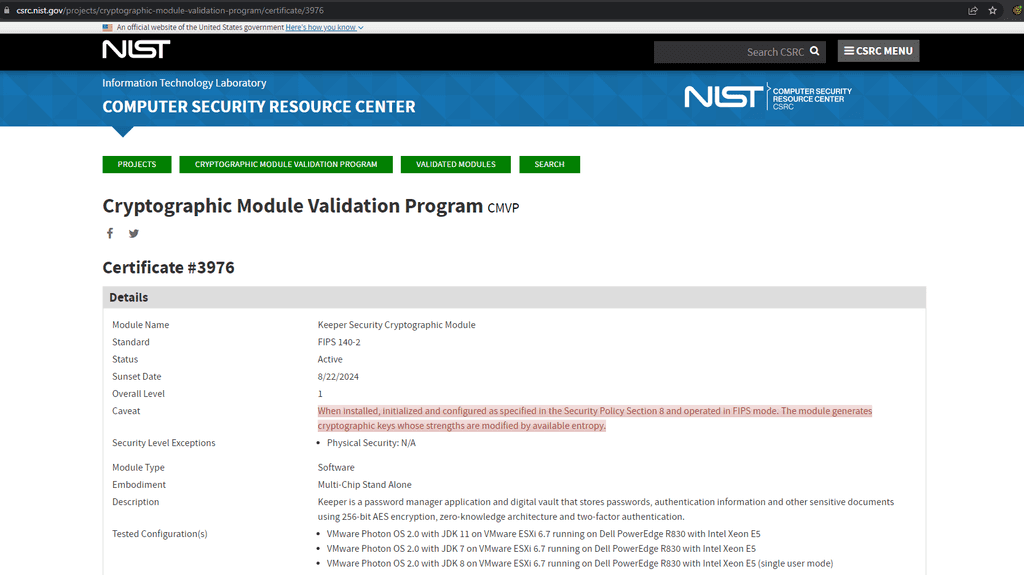
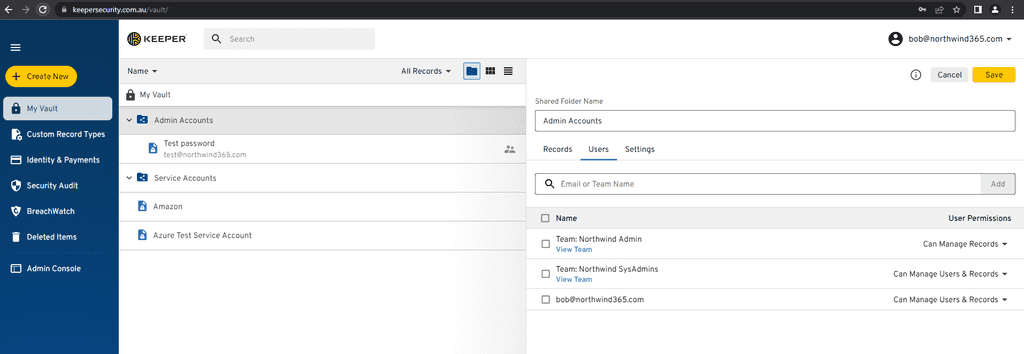
- Keeper - Enterprise level password manager. Different groups of users can be given access to different passwords according to Business priorities.
- 1Password - syncs passwords and personal data across all your devices. It's not quite as slick or capable as many competitors, but it's still an easy-to-use utility
The best enterprise password managers provide a security score for all your enterprise passwords - fix them if your score is low.
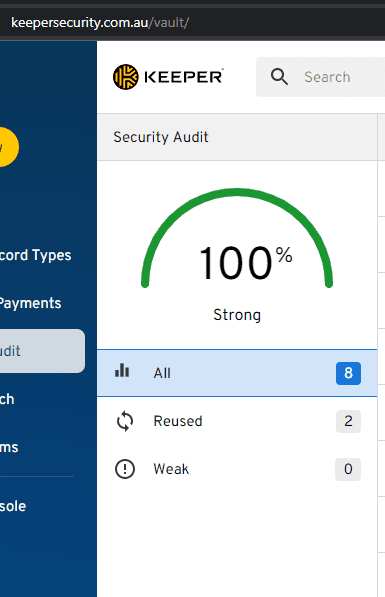
Figure: In Keeper you can see at a glance if insecure passwords are being used They monitor your accounts, regularly checking if they have been released in a breach and notifying you of any problems.
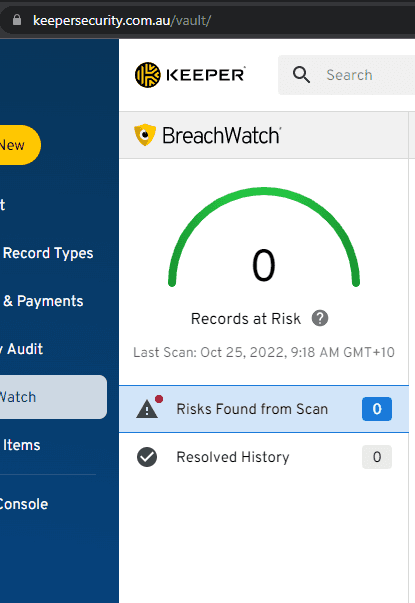
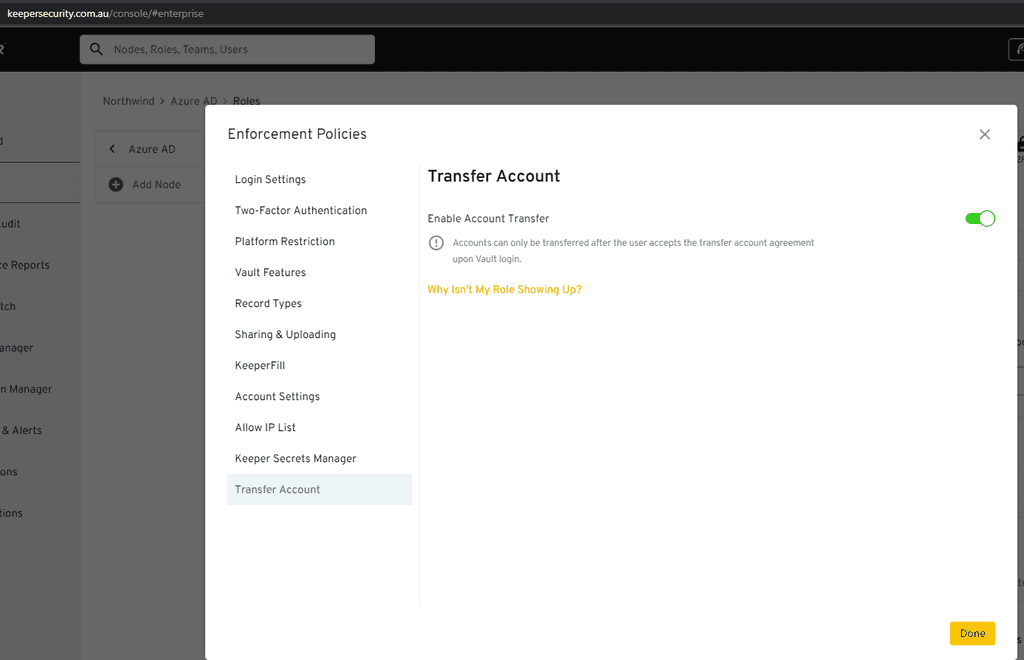
Figure: Keeper quickly shows you if any of your passwords have been released in a breach They also allow administrative control of your accounts. In an enterprise you should be able to transfer any non-shared passwords if a staff member leaves (in case they forgot to share them). Lock their account and expire their master passwords. This is great when a staff member leaves but also super important if they lose a device.
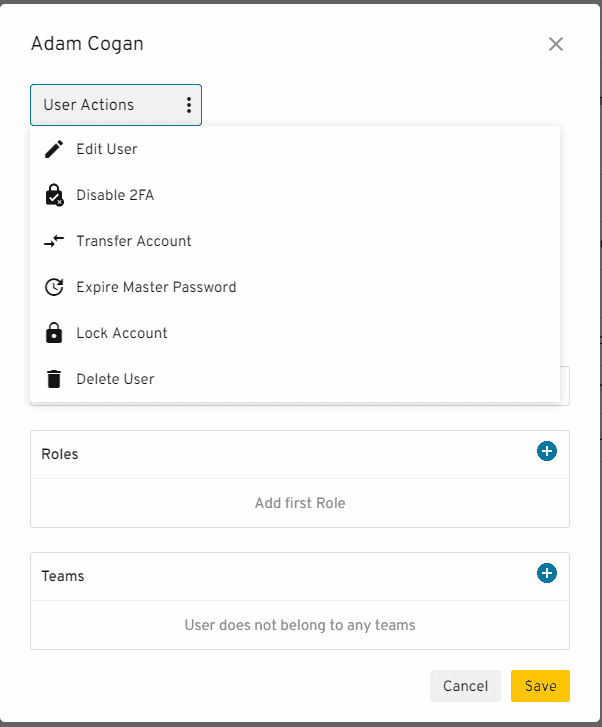
Figure: In Keeper you can lock an account expire a master password or even transfer their passwords
Personal security
You should use them for your personal security as well:
- Keeper - Password vault on unlimited devices and provides secure sharing if you need to give your password to someone else
- 1Password - Syncs passwords and personal data across all your devices. It's not quite as slick or capable as many competitors, but it's still an easy-to-use utility
- Lastpass - Matches the capabilities of other top paid password managers and is easy to use. Platform syncing limitations for the free version make it significantly less useful than it was
- BitWarden - Take control of your online password security and manage private data safely from any location or device
- Dashlane - Put passwords in their place, we'll take care of them for you.
The best way to protect your passwords is to never share them. However, in some cases, sharing passwords may be necessary. In these situations, it is essential to follow a strict password sharing procedure to ensure the security of sensitive information. The key to this procedure is having a powerful password manager to be able to share passwords securely and efficiently.
Learn more about the best password managers.
Do the following, in this order, to securely share passwords:
- Search for the password in a password manager - If you read the rule above, then you have set up a company-wide password manager. Users should be able to search for the passwords they need in the manager, directly. This method is considered ultra secure.
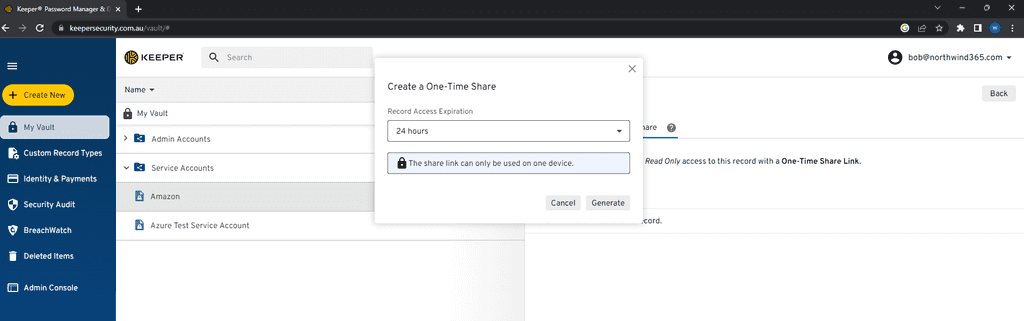
- Share the password via a password manager - Good password managers have one-time password sharing capabilities, e.g. generating a link to the record in the password manager, which can be shared with people who do not have access to the password manager. This method is considered super secure and efficient.
- Share the password via a secure message service such as onetimesecret.com - If you don't have a password manager, you can use free websites that generate links with a message that self-destructs, but this method is considered much less secure. We advise using different mediums to share the password, e.g. username via a Teams message, password via onetimesecret.com
- Share the password via SMS/text - If all previous options fail, we try sharing the password via text. However, this method is much less secure and should only be used as a last resort, if used at all, due to the password being saved forever in an SMS. We advise using different mediums to share the password, e.g. username via a Teams message, password via SMS. The password should be changed after it's all done.
By having a powerful password manager as the foundation of our password sharing procedure, we ensure that our sensitive information is secure and protected against potential data breaches or security threats. While it is always best to avoid sharing passwords, in situations where it is necessary, this password sharing procedure ensures that the sharing is done securely and efficiently.
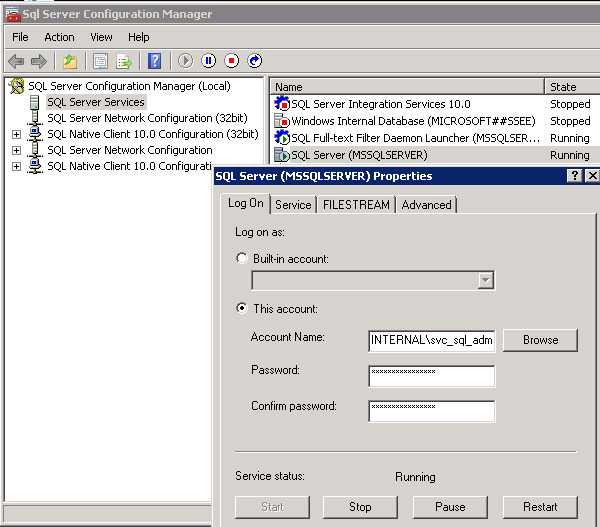
When using service accounts, you should have a specific AD account for each major service.
If an attacker gets into a computer on your network, they can dump hashed credentials of any user that has logged on to that computer from lsass.exe. This is easy to do if you know where to go - thankfully, it is also fairly easy to block!
You can read more about credential dumping at mitre.org, or in this blog post from Microsoft.
Credential Guard was introduced in Windows 10/Server 2016. It runs lsass.exe in an isolated virtualized environment without any device drivers, so that the memory cannot be dumped. Depending on your environment, there are a few ways you can implement Credential Guard.
Group Policy
In a Domain environment, you can roll out Credential Guard with a GPO.
- Go to Computer Configuration | Administrative Templates | System | Device Guard | Turn On Virtualization Based Security
- Enable the policy, and set Credential Guard to Enabled with UEFI lock (recommended), or Enabled without lock.
Note: Enabled with UEFI lock means that Credential Guard needs to be disabled in the GPO and on the device to be turned off. Enabled without lock allows Credential Guard to be disabled just with the GPO.
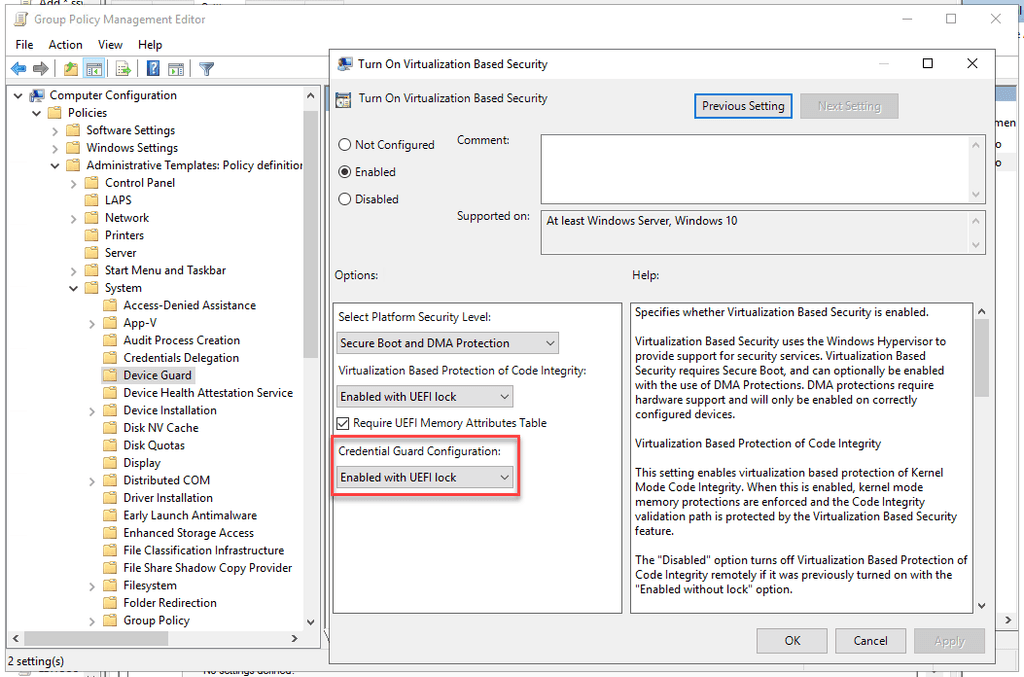
Figure: Credential Guard enabled in a Group Policy object Microsoft Endpoint Manager / Intune
If you use Microsoft Endpoint Manager, you can roll out Credential Guard with an Attack Surface Reduction policy.
- Go to Microsoft Endpoint Manager | Endpoint Security | Attack surface reduction
- Create a new policy, or edit an existing one
- Set Block credential stealing from the Windows local security authority subsystem to Block
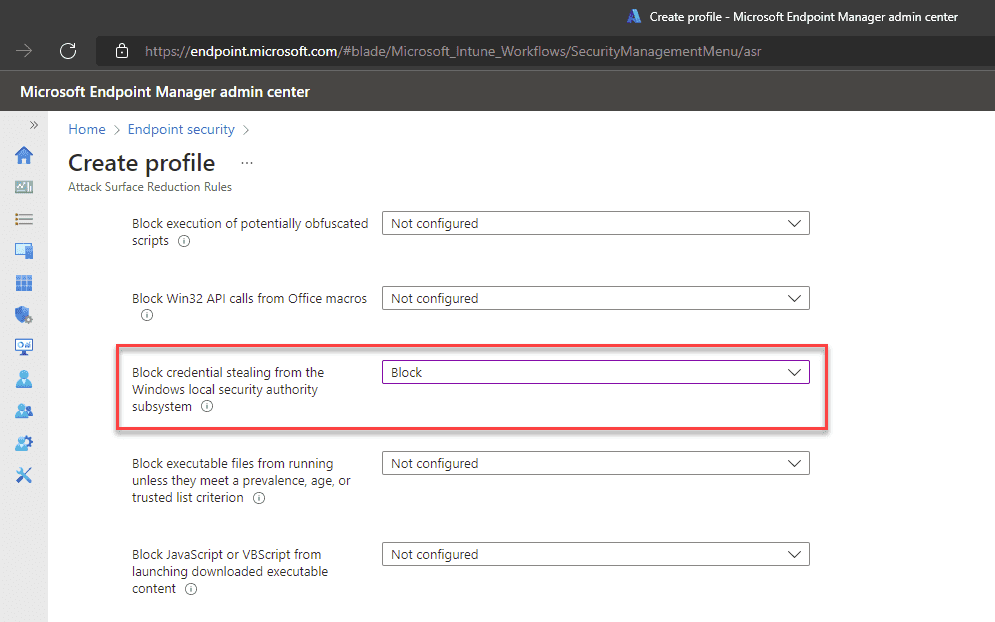
Figure: Credential Guard setting in Microsoft Endpoint Manager More information & other options
For more information or for instructions to implement Credential Guard on a single computer, see Microsoft's documentation on Credential Guard.
For more security tips, read Adam Cogan's 10 Security Tips for CEOs and SysAdmins.
The Open Web Application Security Project (OWASP) is a non-profit charity organization whose sole purpose is to enable other organizations to develop applications that can be trusted. Their most prominent piece of literature is the OWASP Top 10 – a list of the most critical risks found in software. It is a “living” list, which means it is updated as vulnerabilities become known and more or less common.
OWASP Top 10 2021
The current OWASP Top 10 states the following are the top risks for web applications today. Knowing and securing against these will give the biggest bang-for-buck in securing your website.
- Broken Access Control: Insufficient controls in place to implement the principle of least privilege, insufficient access control protections
- Cryptographic Failures: Data transmitted in clear text, sensitive data not encrypted at rest, using weak or broken cryptography algorithms
- Injection: Failure to validate user-supplied data, queries not parameterized
- Insecure Design: Security not considered as a baseline principle, security added as an after-thought (essentially, need to "shift-left" security)
- Security Misconfiguration: Insecure default configurations, misconfigured HTTP headers and verbose error messages containing sensitive information
- Vulnerable and Outdated Components: Packages and dependencies not kept up to date, versions with known vulnerabilities kept in the product
- Identification and Authentication Failures: Brute force attacks, credential stuffing, missing MFA, permits weak passwords, simple password recovery
- Software and Data Integrity Failures: Failure of infrastructure configuration to protect against exploits, e.g. supply chain attacks, dependency package spoofing
- Security Logging and Monitoring Failures: Not logging security events, not monitoring or auditing logs, not raising alerts for suspicious events
- Server-Side Request Forgery: Arbitrarily fetching data from user supplied URLs
Other resources
Protecting against these is a large topic in their own right. There are plenty of resources with information on protecting against these, linked below:
- Troy Hunt – Protecting your web apps from the tyranny of evil with OWASP - This video goes through the OWASP Top 10 in more detail, describing each risk, how to exploit it, and how to protect against it
- OWASP Top 10 - The OWASP home page is a little difficult to navigate but contains fantastic information on the risks and how to protect against them. Use the link above to get details on each of the vulnerabilities, with examples on attacking, “Cheat Sheets” for prevention and risk/impact assessment
- Video: Do you know how to choose an Enterprise Password Manager? | Warwick Leahy | SSW Rules (5 min)
Most organizations store lots of passwords. There is often a need to share these passwords with other staff and these passwords all need to be unique, long and complex. This can all be resolved by using a high quality Enterprise Password Manager. There are a lot of password managers on the market so what features are essential.
These are must have features:
-
Single sign on with Azure AD - It would be ironic for a password manager to require staff to remember another password when the intent is to stop them remembering passwords, so it is essential that a good password manager leverages your existing security information. Also with Azure AD staff already have security groups, they already have MFA and access to very advanced conditional access policies, such as impossible travel and trusted devices.
A good Enterprise Password Manager should take advantage of all the same policies. Also by using auto-provisioning they will automatically gain access to the passwords that an administrator gives them access to when a user is created and given the correct security group access and more importantly lose access to passwords when an account is disabled or they are removed from a security group.
-
Secure and certified - All good password managers should use AES 256-bit encryption and PBKDF2 - generally accepted as being the most secure. This should be certified by an organization like NIST.
-
Internal password sharing - This should be low overhead. Once a user is synced with their groups form Azure they should automatically have access to all of the passwords that they require in the password manager.
-
External password sharing - In the past passwords could be shared using an online service such as onetimesecret.com but that always comes with a risk. That online service could be compromised. A good password manager should allow One-Time sharing from inside the password manager.
-
Administrative control - In the event of a staff member leaving an Administrator should be able to take control of the leaving staff members account. It is easy for a staff member to create a password and not add it to a shared folder. When they leave an Administrator needs to be able to check those passwords and keep any passwords that might be required by the organization. All good Enterprise Password Managers provide free family plans for their staff so none of these passwords should be personal.
-
Reporting - Good reporting is essential. Easily checking that all the passwords used in the organization are unique and also complex is very important. Not only that but if a login has been compromised and released on the dark web then it's important that an Administrator is notified about it and can act on it.
-
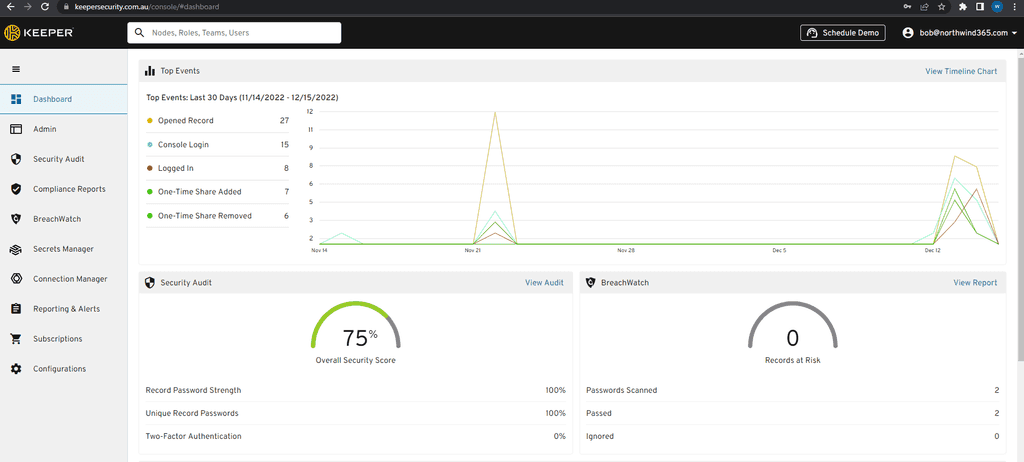
Auditing access data is crucial for any enterprise to ensure security and compliance. Having an audit trail provides visibility into who accessed what data, when, and from where. An effective enterprise password manager should be able to offer this feature.
For example, Keeper (an enterprise-focused password product) is a leading enterprise password manager that offers a comprehensive auditing feature. It provides administrators with detailed logs and reports on user access, ensuring transparency and accountability.
Why is Auditing Access Data Important?
- Security Oversight: Monitoring who accesses data and when can identify potential security breaches or unauthorized access attempts.
- Compliance: Many industry regulations mandate businesses to maintain a detailed audit trail of data access, especially for sensitive or personal data.
- Accountability: An audit trail holds users accountable for their actions, discouraging misuse or unauthorized changes.
Finding Audit Data for a Particular Folder or Record in Keeper
-
Get the UID of the folder/item: First get the UID of the folder or item that you want to audit.
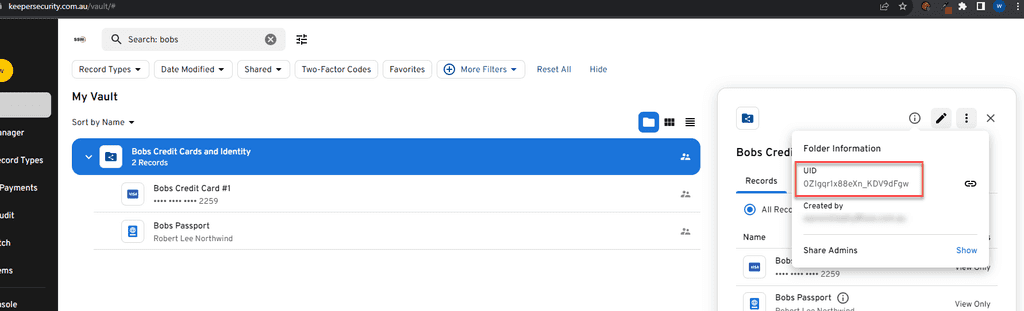
Figure: First get the UID of the Folder/item for report - Login to the Keeper Admin Console: Now switch to Keeper's admin console and login.
-
Navigate to the 'Reporting & Alerts' Section: This allows an admin to create a custom report. Then add a new report.
Tip: You can then create an alert from that report if required.
-
Apply Filters: You can filter the audit logs by various criteria, including user, date range, or specific activities. To find audit data for a particular folder or record, input its name or related keyword in the search or filter option.
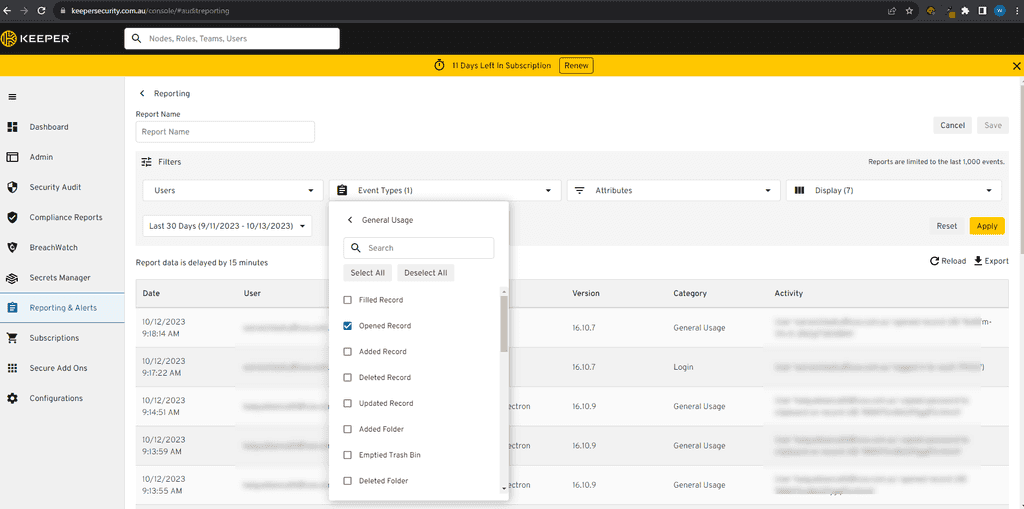
Figure: Filter by the Event Type 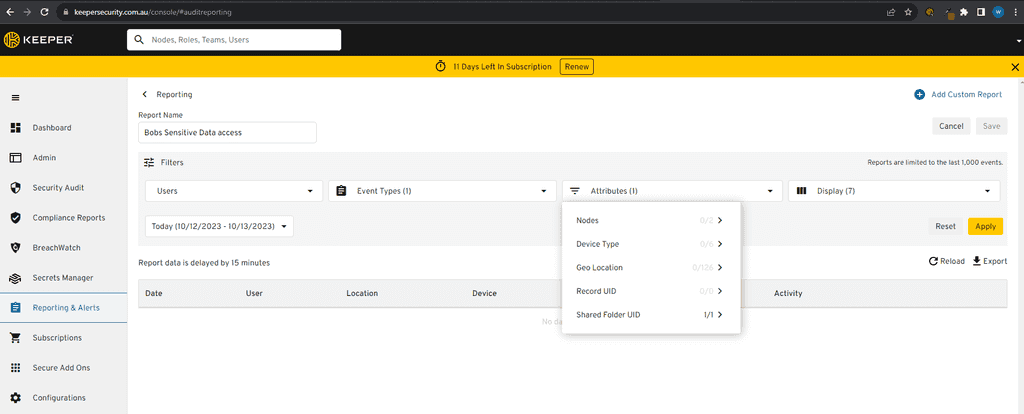
Figure: Filter by Attributes - Category first 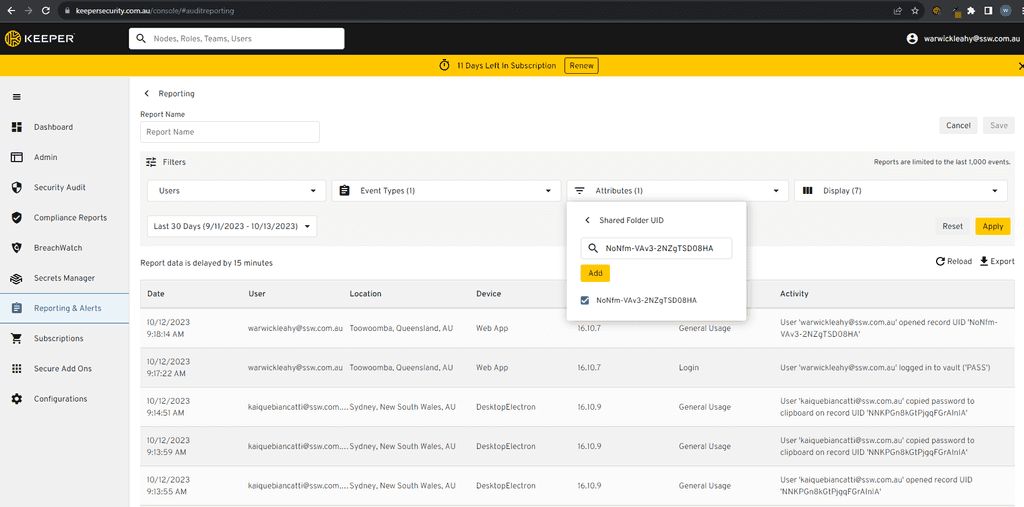
Figure: Filter by Shared Folder / Item UID (Obtained from step 1) - Filter Time/User: Choose any other filters such as Time Period or User and click apply.
-
Review the Logs: Once filtered, you'll see a list of actions related to the chosen folder or record. This will include details like who accessed it, when, and from which device or location.
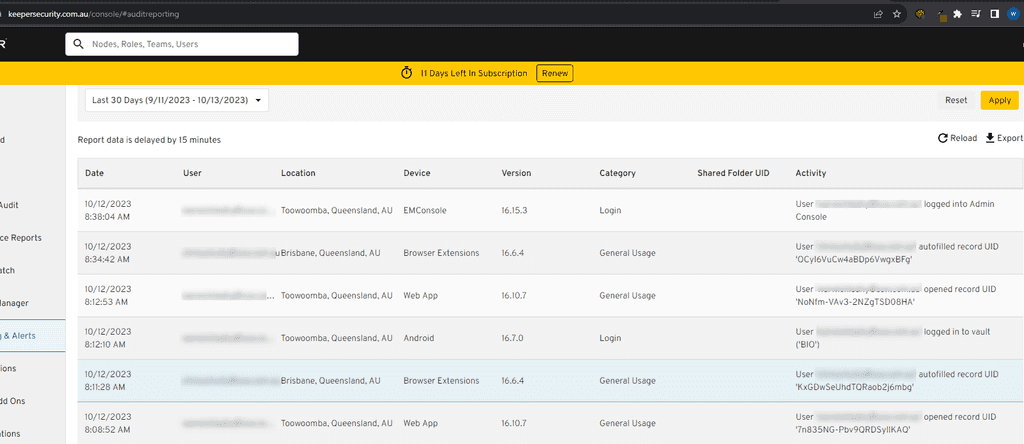
Figure: View the audit log - Export or Save: If you wish to keep a record of the audit data outside of Keeper, you often have the option to export the data to various formats or save it for later review.
When selecting an enterprise password manager, auditing capabilities should be a priority. Keeper serves as a strong example of how detailed and user-friendly audit features can enhance security and transparency in data management.
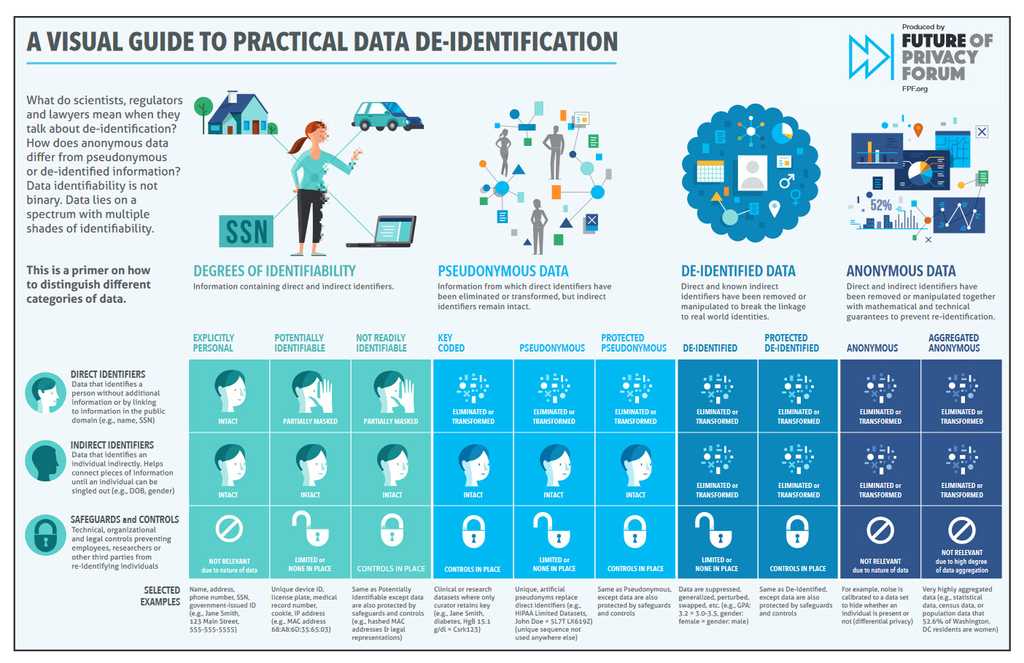
Ensuring the privacy and security of client data is a critical responsibility in today's digital age. With increasing data breaches and the rise of cyber-attacks, it is imperative to take proactive measures to protect client information. De-identifying data is a key step in reducing the risk of data breaches and safeguarding the privacy and confidentiality of client information.
When working with client data, you should do the following:
- Avoid copying client data to local servers in the first place. If it is unavoidable to copy the data, it is crucial to ensure that the data is de-identified before it is transferred. This helps to reduce the risk of unauthorized access to client information and protects against data breaches.
-
If copying data is not avoidable, only copy de-identified data. There are several tools available for de-identifying data, including:
- Data masking software - Data masking software, such as Informatica MDM, K2View and IRI FieldShield, helps to protect client information by obscuring sensitive data with randomized characters, making it unreadable to unauthorized users.
- Redaction tools - Redaction tools, like Adobe Acrobat Pro, Ibjective Redact and Egress Respond, allow you to remove sensitive information from documents by blacking out or obscuring the data.
- Pseudonymization tools - Pseudonymization tools, such as Talend, replace sensitive data, such as personal identification, with generic identifiers, helping to protect the privacy and confidentiality of client information.
- All-in-one de-identification software - For a complete solution, consider using all-in-one de-identification software, such as Anonymize, brighter AI, the Informatica suite, and Privacy1, which provides a range of tools and features for de-identifying data, including data masking, redaction, pseudonymization, and more.
- If you must work with live data, it is recommended to use Azure. Azure is a secure and compliant cloud computing platform that provides a safe and secure environment for processing and storing client data. With Azure, you can ensure that client information is protected against unauthorized access and data breaches, while also meeting regulatory requirements and industry standards.
The Future of Privacy Forum has an easy guide to practical da de-identification:
Azure Active Directory (AAD) Identity Protection's Sign-in risk policy helps automatically protect your users from risky sign ins to their accounts.
Azure AD has many built-in solutions to protect legitimate users from malicious actors trying to sign in to their accounts via Azure AD, one of them being Sign-in risk policy.
This policy can either fully block access or require a multi-factor authentication (MFA) for the user to be able to login, depending on the the sign-in risk level (High, Medium and above or Low and above).
The level is determined automatically by a series of factors, including:
- Impossible travel e.g. If a user has logged in from Australia and then authenticates from Europe in the next 5 minutes, an impossible travel to physically make
- Unfamiliar sign-in properties e.g. If a user has logged in from a location that he never logged on from before
- And other, constantly updated factors.
When setting this up, you can also choose to apply this to all your users, selected individuals or groups, and exclude users.
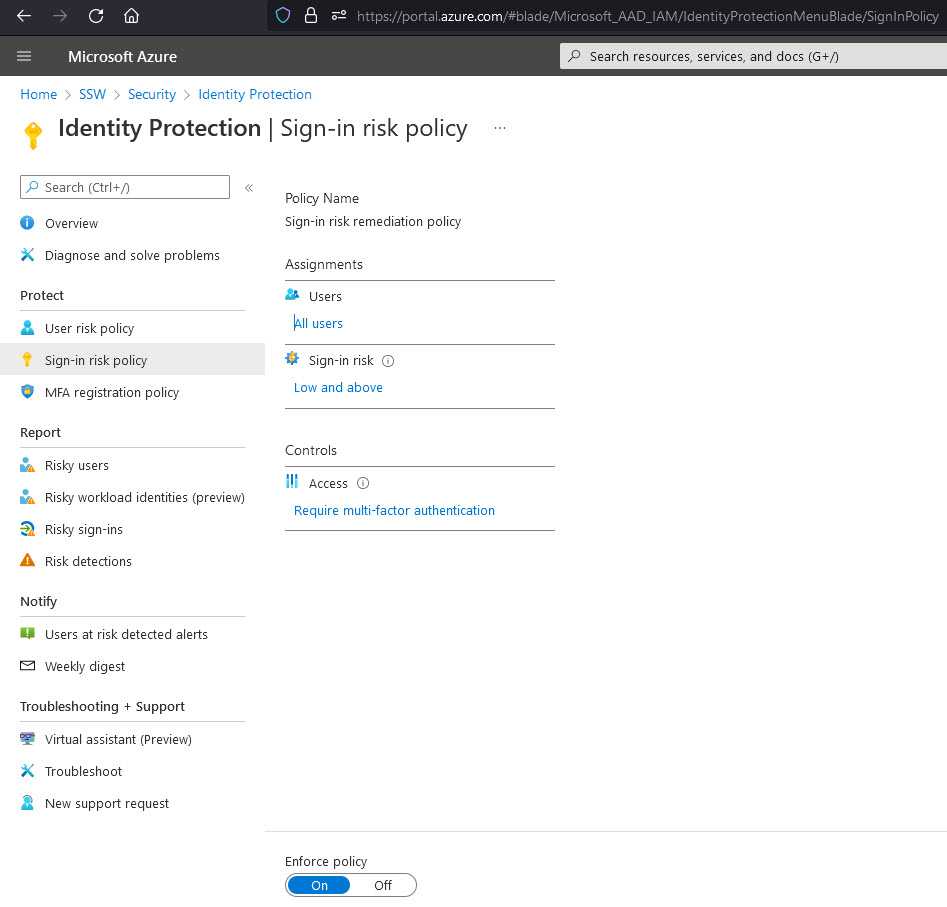
Good Example - All users with a risk of Low and above will be prompted for MFA authentication You can read more on how to enable these policies on Configure and enable risk policies
Entra ID Protection's user risk policy helps automatically protect your users from risky behaviour on their accounts.
Entra ID has many built-in solutions to protect legitimate users from malicious actors trying to sign in to their accounts via Entra ID, one of them being user risk policy.
This policy can either fully block access or require a password reset for the user to be able to login, depending on the the sign-in risk level (High, Medium and above or Low and above).
The level is determined automatically by a series of factors, including:
- Atypical travel e.g. If a user has logged in from Australia and then authenticates from Europe in the next 5 minutes, an impossible travel to physically make
- Unfamiliar sign-in properties e.g. If a user has logged in from a location that he never logged on from before
- And other, constantly updated factors
When setting this up, you can also choose to apply this to all your users, selected individuals or groups, and exclude users.
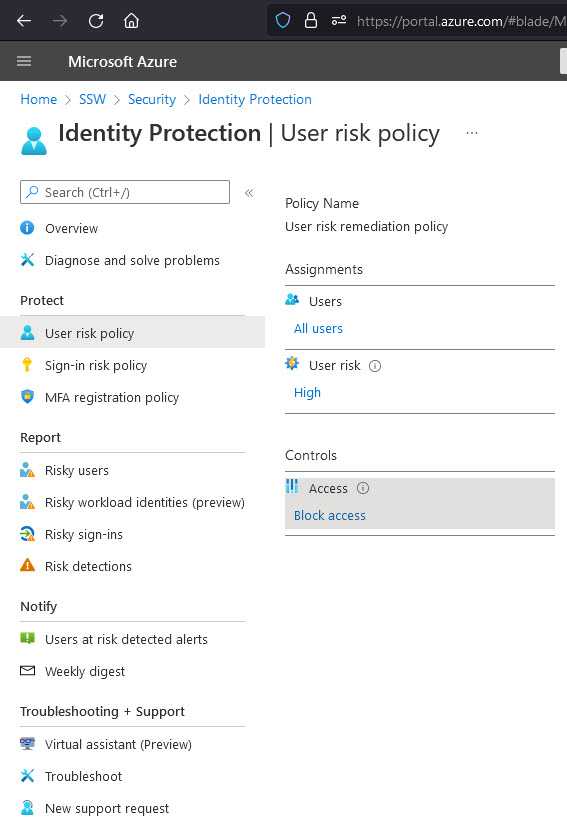
Good example - All users with a risk of High will be blocked from signing in You can read more on how to enable these policies on configure and enable risk policies documentation.
When integrating an external authentication provider (IdentityServer, Azure AD or Microsoft Entra ID etc.) with an existing ASP.NET Core application which uses ASP.NET Core Identity, challenges arise due to different user identification systems.
On the ExternalAuthProvider side, users are typically recognised by a unique Subject Id within their issued token after authentication. In contrast, an application's existing user store might use its own unique user ID, possibly combined with other data.
The above discrepancy creates the need to effectively map or correlate the the user with a Subject Id from the ExternalAuthProvider to the corresponding user within the app's user store.
⚠️ Warning: The approach described here assumes that the user's email address is verified. With some external providers, such as Apple, you can trust that the email is verified. For others, such as Microsoft, the email property can come from a freely editable field and should be treated as unverified. Email addresses from unverified providers should be verified within your application. You should always ensure a user owns an email address before relying on it to grant access to data.
Two essential scenarios arise when integrating the ExternalAuthProvider:
1. Pre-existing company users
Addressing users already registered with company emails in the existing application user store now authenticating through the ExternalAuthProvider:
SubId check
Begin by verifying if the user has an external login associated with the SubId from the ExternalAuthProvider in your application's user store using the
FindByLoginAsync()method. If found, proceed with authentication by handling the request gracefully.var existingUserByExternalLogin = await _userManager.FindByLoginAsync(EXTERNAL_AUTH_PROVIDER, subId);Existing users by email verification
If there's no associated SubId, check if the email (provided by the ExternalAuthProvider during authentication available as one of the claims in the JWT token) exists in your application's user store.
var userByUserName = await _userManager.FindByEmailAsync(emailFromIdentityServer);Figure: Retrieving existing user by using the Email claim from the JWT token utilising the FindByEmailAsync() from the UserManager class.
Users known to the application but not authenticated via ExternalAuthProvider
Retrieve the SubId from the JWT provided by the ExternalAuthProvider. Use ASP.NET Core Identity's
AddLoginAsync()method to associate this SubId as an external login with the user's record.var subId = token.Claims.FirstOrDefault(c => c.Type == "sub"); await _userManager.AddLoginAsync(newUser, new UserLoginInfo(EXTERNAL_AUTH_PROVIDER, subId));Note: In the example above the "EXTERNALAUTHPROVIDER" is a constant which contains the identifier for your external authentication provider. e.g. IDENTITYSERVEREXTERNAL_LOGIN = "IdentityServer"
Future Authentications
For all subsequent logins, employ the
FindAsync(new UserLoginInfo())method.✅ Benefits
- Seamless authentication experience for existing users
- Avoids custom fields in the ApplicationUser model, leveraging existing ASP .NET Identity Core methods like
AddLoginAsyncandFindAsync
2. New ExternalAuthProvider registrants
Incorporating users who are new to both the ExternalAuthProvider and the application:
Email verification
Check if the email provided by the ExternalAuthProvider during authentication exists in your application's user store by using ASP .NET Identity Core methods like
FindByEmailAsync(). If it doesn't, this indicates the user is new.var existingUser = await _userManager.FindByEmailAsync(emailFromIdentityServer);User creation & SubId association
Register by creating a new user in your application's store using claims provided by the ExternalAuthProvider (e.g., first name, last name, email).
var newUser = new Domain.Entities.ApplicationUser { UserName = token.Claims.FirstOrDefault(c => c.Type == "email");, FirstName = token.Claims.FirstOrDefault(c => c.Type == "first_name");, LastName = token.Claims.FirstOrDefault(c => c.Type == "given_name");, CreatedDateTime = DateTime.UtcNow, Culture = "en", }; // Create new user in the database var createNewUserResult = await _userManager.CreateAsync(newUser);Note: In the example above extraction of claims may vary based on how you access the token.
Extract the SubId from the JWT token (typically the "sub" claim) and use ASP .NET Core Identity's
AddLoginAsyncmethod to associate this SubId as an external login with the newly created user record.var subId = token.Claims.FirstOrDefault(c => c.Type == "sub"); await _userManager.AddLoginAsync(newUser, new UserLoginInfo(EXTERNAL_AUTH_PROVIDER, subId));Future Authentications
Finally for all subsequent logins use the
FindByLoginAsync()method to check if the user already exists.var existingUser = await _userManager.FindByLoginAsync(EXTERNAL_AUTH_PROVIDER, subId));✅ Benefits
- Facilitates the seamless integration of new users to the ecosystem.
- Consistent user experience for new users, leveraging native ASP .NET Core Identity methods.
- Streamlined process, avoiding manual or ad-hoc registration steps.
Stateless authentication with JWT overcomes traditional session-based limitations by eliminating server-side session storage, thereby boosting scalability and security. This approach simplifies user verification across distributed systems without the scalability and security concerns associated with the session based approach, making it more aligned with modern web development needs.
Video: Why is JWT popular (5 min)Modern stateless authentication, leveraging JSON web tokens (JWT), offers a scalable solution for managing user authentication without server-side storage. The OIDC framework, building on OAuth 2.0, standardizes interactions between authentication services and users. JWTs, containing a header, payload, and signature, ensure data integrity and authentication validity. Issued by trusted identity providers, these tokens facilitate user identification in applications, moving away from traditional session-based methods. This approach enhances scalability and user management, aligning with current web development trends.
The Process of Stateless Authentication with JWT
User Authentication
- The user authenticates to the identity provider
- Upon successful authentication, the provider generates a JWT, which includes claims about the user and is signed with a secure key
- The JWT is then returned to the client application, usually via an HTTP response
Token Storage
- The client application receives the JWT, and must store and handle it securely to reduce the risk of compromise
Authorized Access
- For subsequent requests to your resource available at your application backend server, the client includes the JWT in the request headers as a Bearer token
- The server, upon receiving a request with a JWT, verifies the token's signature and the validity of its claims against the authority
- If the token is valid, the server grants access to the requested resource which in most cases is an API
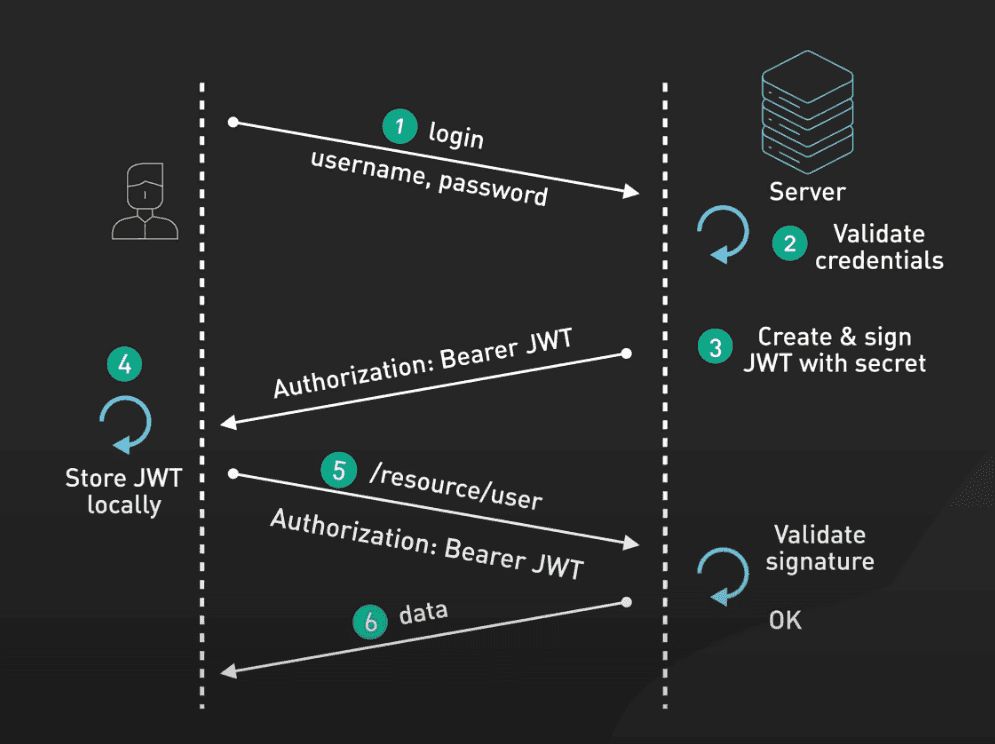
Figure: JWT Authorisation Flow Token Expiry and Refresh Mechanism
- JWTs typically have an expiration time set by the issuer; once expired, the user must re-authenticate to obtain a new token
- Often, a refresh token mechanism is employed, where a longer-lived refresh token is issued alongside the JWT
- The refresh token can be used to sliently obtain new access tokens without requiring the user to re-authenticate, enhancing the user experience while maintaining security
Benefits of JWT in Stateless Authentication
- Scalability: As the resource doesn't store session data, it can easily handle requests from a large number of users without a significant impact on performance
- Flexibility: JWTs can be used across different domains and in various architectures making them suitable for modern, distributed applications
- Performance: Carrying relevant user information within tokens can reduce database queries, improving the overall performance of the application
Security Considerations for JWT Authentication
Proper security measures are essential in handling JWTs to prevent unauthorized access and breaches:
- Sensitive Information: Avoid storing sensitive data in JWT payloads as they are not encrypted and can be exposed to unauthorized parties
- Secure Storage: Prefer HttpOnly cookies over local storage for JWTs to mitigate the risk of Cross-Site Scripting (XSS) attacks; HttpOnly cookies enhance security by restricting access to tokens via JavaScript
- Token Expiry: Implement short-lived JWTs to reduce the risk window in case of token compromise - Short expiration times necessitate more frequent token renewal, enhancing security
- Transmission Security: Use HTTPS to ensure encrypted communication between client and server, protecting token data during transit
- Validation and Revocation: Validate JWTs on each request to verify their integrity and authenticity also consider token revocation mechanisms for additional security, such as maintaining a list of invalidated tokens
Adopting these practices helps maintain the integrity of JWT-based authentication and protects against potential security threats.
Understanding and implementing modern stateless authentication with JWTs is crucial for developing secure and scalable web applications. By following the best practices for token management and security, developers can build robust authentication systems that cater to the needs of modern web applications.
For more insights and technical implementations, consider exploring additional resources such as Auth0's guide on Stateless Sessions for Stateful Minds and LogRocket's blog on JWT authentication best practices.
Sharing sensitive information is an essential part of any business, however sharing information securely is equally important, especially when files, videos or images can contain sensitive information. Without proper precautions, sensitive data can inadvertently become accessible to unauthorised parties, creating significant risks.
Best practices for sharing sensitive information
When sharing files which may include sensitive content, such as discussions about clients or current security issues for a product, follow these steps to keep them secure:
1. Choose a secure hosting platform
- Option 1 - SharePoint for files / Microsoft Stream for videos (Recommended) When recording videos via Teams, you can automatically uploaded the recordings to Microsoft Stream, this ensures that the videos remain private within your organization. SharePoint provides similar controls for document sharing and integrates seamlessly with other Microsoft 365 tools like Microsoft Stream.
- Option 2 - Google Drive When using the Google Suite users can upload files to Google Drive for the organisation and restrict access similarly to the Microsoft 365 suite.
- Option 3 - YouTube videos set to private visibility For teams not using Microsoft 365 products, YouTube's "Private" option can be used to share videos securely. Be cautious, as this approach can accidentally expose videos publicly if you are not careful.
2. Restrict access to authorized individuals
Ensure that only the relevant team members or clients can view sensitive information:
- Set file or folder permissions based on specific roles or groups
- Periodically review permissions to remove access for users who no longer need it
3. Use data security techniques
For extra protection, particularly when the information might be shared more broadly:
- Redact information - Replace or black out sensitive details in documents or screenshots
- Generalise context - Use placeholders (e.g., "Client A" or "Project B") instead of real names and specifics
4. Securely share links
If you need to securely share links, please see these rules:
- Do you know how to securely share your passwords?
- Do you know the best way to share a password externally?
5. Regularly review privacy policies on hosting services
Platforms like SharePoint and Stream adhere to strict security standards, but regular audits of your privacy settings and hosting policies help ensure continuous compliance with organizational or legal requirements.
Example
Scenario: You need to share a Sprint summary video with your team, and it contains client-sensitive information.
Steps:
- Upload the video to Microsoft Stream or SharePoint
- Set permissions to allow viewing only for specific team members
- Use the platform's secure sharing link feature, ensuring it's time-limited
When users create a password during sign-up, they often make mistakes due to typos, especially on mobile devices. This can lead to frustration, failed login attempts, and the need to reset passwords, creating a poor user experience.
Adding an eye toggle icon solves this problem by allowing users to verify their password before submission. This simple feature reduces errors, minimizes the likelihood of password resets, and enhances usability and accessibility without compromising security.
Penetration testing is an important part of maintaining secure networks and systems - it provides a simulated and controlled way to test the strength of your security. When all your services and infrastructure are exposed to the world, how can you make sure you're safe?
Video: Do you take Penetration Testing seriously? | Rob Thomlinson & Oliver Judson | Rules (8 min)What is Penetration Testing?
Penetration Testing is a simulated cyberattack performed by security professionals to evaluate the security of the services, systems, and networks of an individual or company. It helps companies identify vulnerabilities in their security systems, access the potential impact and damages, and steps to fix these vulnerabilities.

Figure: Penetration Testing is an important part of securing your systems Why do we need Penetration Testing?
It is important for several reasons:
- By mimicking real attackers, penetration testers can identify vulnerabilities and, most importantly, provide solutions to fix these vulnerabilities before they can be exploited by bad actors.
- Using an external tester eliminates implicit biases and assumptions, avoids conflict of interest, and uncovers security flaws that may be overlooked internally.
- The cost to secure yourself from an attack is far cheaper than the consequences of an attack.
- Evaluates the quality of existing policies, tools and procedures.
- Evaluates incident response measures by measuring how well the security team detects, responds to, and mitigates attacks.
- As attack techniques evolve, penetration tests help companies adapt and defend against emerging threats and vulnerabilities.
How can you improve your security?
Great company security starts with great user security. Here are some of the most valuable ways you can help defend against an attacker:
- Multi Factor Authentication – more than one authentication method means more layers of security
- Use password managers to generate unique passwords for every service (and auto-fill them)
- Lock your laptop when you leave your desk. For Windows users, check out DynamicLock
- Avoid malware by not clicking on suspicious links and making sure the person is who they say they are
- Report potential breaches to SysAdmins, whether it's your personal account or a company account
Different types of penetration tests
There are 5 common penetration tests most businesses will engage a 3rd party for:
- Internal penetration testing - A consultant will simulate an attacker who has managed to access your internal network to evaluate security and configuration issues in your network, systems and endpoints
- External penetration testing - A consultant would simulate an attacker trying to access any device or service that a business uses which would provide them with access to an organisations resources
- Wi-Fi penetration testing - A consultant evaluates the security and configuration of your offices wireless networks
- Application penetration testing - A consultant looks for vulnerabilities and flaws in the design of an application, this can be done by identifying issues with API's, authentication, data exposure or
- Physical penetration testing - A consultant tests the physical security of an office to see how easy it is to gain access to restricted areas
What are the recommended tools to use?
We have a few rules that cover the best cybersecurity tools for developers and SysAdmins:
- For Developers: Do you use the right cybersecurity tools when writing code?
- For SysAdmins: Do you use the right cybersecurity tools as a Sysadmin?
Cybersecurity threats are constantly evolving, as a sysadmin, it's your job to stay ahead. Using the right tools can mean the difference between a secure environment and an incident. Relying only on the default security features is not enough these days, proactive defence is key.
Essential Cybersecurity tools for Sysadmins
A well-rounded cybersecurity strategy should include tools for:
1. Active Directory Security
Active Directory Security tools are used for on-demand secrity assessments of the environment these tools can prevent misconfiguration of an AD Environment.
✅ Recommended tools:
- PingCastle
- BloodHound
2. Vulnerability management
Provides Centralised reporting for all potential vulnerabilities in a companies system.
✅ Recommended tools:
- Nessus
- Qualys
- OpenVAS
3. Patch management
Allows SysAdmins to deploy regular patches to company hardware.
✅ Recommended tools:
- Patch ManageEngine
- WSUS (Windows Server Update Services)
4. Multi-Factor Authentication (MFA)
Ensures users are protected even if their passwords are breached.
✅ Recommended tools:
- Duende Identity Server
- Microsoft Entra ID (formerly Azure AD)
- Okta
- Duo Security
5. Privileged Access Management (PAM)
Protects companies most sensitive systems and ensurses that they only have the necessary level of access to complete tasks.
✅ Recommended tools:
- CyberArk
- BeyondTrust
6. Automated Backup Solutions
Automated backup solutions and backup solutions that promote immutable backups can protect companies from ransomware attacks.
✅ Recommended tools:
- Veeam
- Acronis
- Azure Backup
7. Endpoint Security Suites
Endpoint security tools help protect companies from currently infected devices.
✅ Recommended tools:
- Microsoft Defender for Business
- Bitdefender
- Sophos
8. Email filtering & phishing protection
Email and phising tools prevent organisations from receiveing malicious emails.
✅ Recommended tools:
- Microsoft Defender for Office 365
- Proofpoint
- Mimecast
9. Penetration testing
These are specialised tools used to test a wide variety of scenarios
✅ Recommended tools:
- Metasploit
- Nmap
- Kali OS
10. SIEM (Security Information and Event Management)
SIEM tools allow us to create a centralised view of all security and event logs in an organisation
✅ Recommended tools:
- Microsoft Sentinel
- Splunk
11. EDR (Endpoint Detection and Response)
EDR Tools allow us to identify systems at risk and run automated fixes for known issues.
✅ Recommended tools:
- Microsoft Defender for Endpoint
- CrowdStrike Falcon
12. Adversary Simulation
Specialised tools to simulate cybersecurity threats in an organisation
✅ Recommended tools:
- Cobalt Strike
- Havoc Framework
13. Web Auditing tools
Tools to audit web security.
✅ Recommended tools:
Implementing a strong cybersecurity strategy
Simply having these tools isn’t enough, sysadmins should:
- Conduct penetration testing both internally and externally
- Regularly review logs and security alerts
- Train users on security best practices to reduce human error
By using the right cybersecurity tools and adopting a proactive approach, sysadmins can keep their companies ahead of evolving cyber threats.
Security should never be an afterthought when writing code. Every year, developers introduce vulnerabilities that lead to data breaches, financial losses, and reputational damage. The right cybersecurity tools can help identify security risks early, prevent attacks, and ensure compliance with security best practices.
Essential cybersecurity tools for developers
To write secure code, developers should use a combination of tools that cover different aspects of application security:
1. Static Application Security Testing (SAST) Tools
SAST tools analyse source code for security vulnerabilities without executing the program. They help catch common issues such as SQL injection, cross-site scripting (XSS), and insecure dependencies.
✅ Recommended tools:
- SonarQube (for code quality and security)
- Semgrep (lightweight static analysis)
- Checkmarx (enterprise-grade security scanning)
2. Dynamic Application Security Testing (DAST) tools
DAST tools test running applications by simulating attacks. They help identify vulnerabilities that might not be visible in the source code, such as misconfiguration and runtime security flaws.
✅ Recommended tools:
- OWASP ZAP (open-source web application security scanner)
- Burp Suite (penetration testing toolkit)
3. Software Composition Analysis (SCA) tools
Most applications rely on open-source dependencies, which may contain security vulnerabilities. SCA tools scan dependencies for known vulnerabilities and recommend patches.
✅ Recommended tools:
- Dependabot (GitHub-integrated automated dependency updates)
- Snyk (real-time vulnerability detection and fixes)
- OSS Index (open-source security scanner)
4. Secrets Detection tools
Developers sometimes accidentally commit API keys, passwords, or credentials to repositories. Secrets detection tools scan code to prevent such leaks.
✅ Recommended tools:
- GitGuardian (real-time secret scanning for repositories)
- TruffleHog (deep secrets detection in git history)
5. Container and Cloud Security tools
If your application runs in containers or the cloud, security must extend beyond your code.
✅ Recommended tools:
- Docker Scout (container image vulnerability scanning)
- Kube-bench (Kubernetes security benchmarking)
- AWS Inspector (security assessment for cloud workloads)
6. Code Signing and Supply Chain Security
With software supply chain attacks on the rise, developers should ensure that their code and dependencies are verified and secure.
✅ Recommended tools:
- Sigstore Cosign (secure code signing)
- in-toto (software supply chain verification)
7. API Security Testing tools
APIs are a common attack vector, and testing them for security vulnerabilities is crucial. API security testing tools help developers validate authentication, authorization, and request handling.
✅ Recommended tools:
- Insomnia (secure API testing with authentication and encryption support)
- Postman (API development and security testing)
- OWASP Amass (API reconnaissance and security analysis)
Pro tip: Automate security in CI/CD pipelines
Set up your cybersecurity tools to run automatically on every pull request. This ensures security checks are continuous and prevent vulnerabilities from slipping into production.
By integrating these cybersecurity tools into your development workflow, you can write secure code, protect user data, and reduce the risk of security incidents.
If you accidentally include confidential information in a GitHub Issue - whether it’s a password, API key, or private business details - the obvious thing to do is edit the issue and delete the sensitive content.
But that’s not enough.
GitHub retains a full revision history for issues and comments. This means others can still view older versions and recover the compromised data.
To protect your company and users, you must check and delete the specific revisions that exposed the information.
Finally, it's important to leave a transparent comment in the issue confirming that sensitive content was removed, and where it appeared (e.g. in a video, image, or text block).
Steps to properly remove confidential data
- Edit the Issue or comment
Immediately remove any visible confidential data from the issue body, comment, or image attachment. - Review all revisions
Click the “edited” tag next to any edited comment or issue to see its history. Note which revision contains the sensitive info. -
Delete the affected revision
- If you have permission, delete the comment or attachment that contained the data.
Figure: Delete revisions so compromised data is fully removed - If you can’t delete it yourself, contact your repository owners or admins and ask them to remove it.
- If the revision still can’t be deleted (e.g. issue body history), contact GitHub Support and provide:
- The repository name
- A direct link to the issue or comment
- A description of the confidential information
- A request to delete the specific revision(s)
- If you have permission, delete the comment or attachment that contained the data.
-
Add a note for transparency
In the issue description or a comment, add a message like:
"‼️ CONFIDENTIAL INFORMATION REMOVED The affected content was in a: screenshot / comment / video / etc."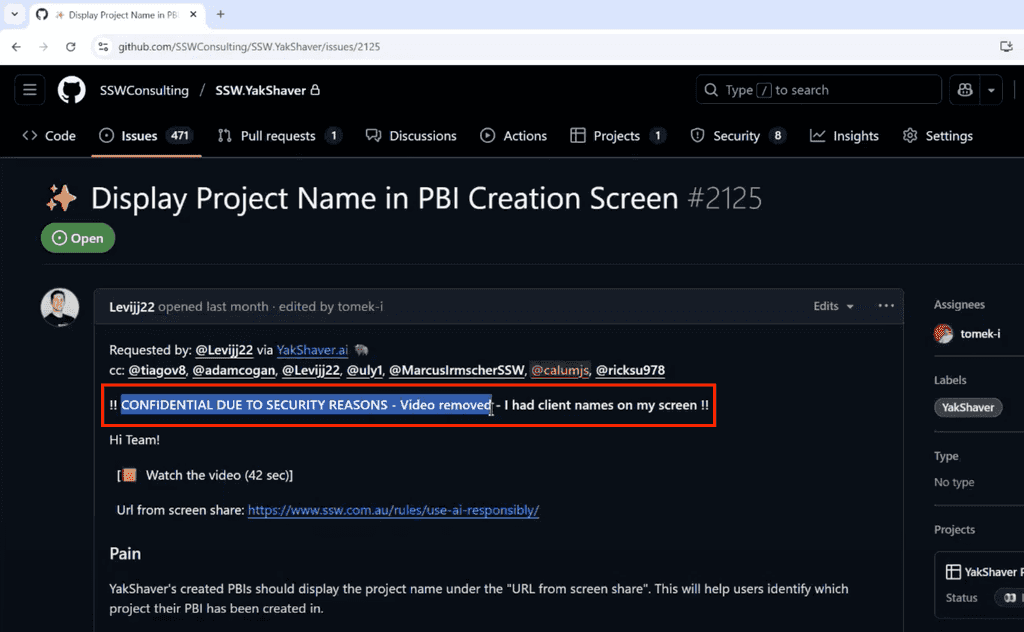
Figure: Inform about deletions mentioned what it was
Tips to prevent future issues
- Avoid uploading full-screen screenshots or videos that contain internal tools, passwords, or customer data
- Use redaction tools before sharing media
- Always review YakShaver recordings and generated content
- Enable 2FA and rotate keys immediately if any credentials were exposed
- Edit the Issue or comment