System Administrators (SysAdmins) are the lifeblood of any business. They mantain the infrastructure, networks and systems and cloud of businesses. This is why we have developed these standards for better System Administrators.
If you still need help, visit our Network Architecture consulting page and book in a consultant.
At some point every business will experience a catastrophic incident. At these times it is important to have a plan that explains who to contact, the priority of restore and how to restore services.
At the time of a disaster, you should have a few objectives established and measure some results - The objectives are RPO (Recovery Point Objective) and RTO (Recovery Time Objective); and the measurements to take are RPA (Recovery Point Actual) and RTA (Recovery Time Actual).
It's recommended to practice your disaster recovery at least once every 12 months. This way you make sure that you are investing in the minimum amount of required resources, and that your plan actually works.
For unplanned outages, see Outage - Do you have an unplanned outage process?
If your servers are down or have to go down during business hours you should notify the users at least 15 minutes beforehand so you will not get 101 people all asking you if the computer is down.
For short outages (under 15 minutes) that only affect only a few people (under 5 people), or are outside of business hours, then IM is the best method. If you use Microsoft Teams, a quick message will do.
Note: If they are not online on Teams, then they can't complain that they were not warned.
For extended or planned outages, or if you have a larger number of users (50+), email is the suggested method.
During your course of being a SysAdmin, you will come across many unplanned outages. Some of them will impact BAU (Business as usual) and others will just be minor service outages. Do you know what to do in the event of these outages?
For any kind of backups, it is important to log a record on success so you can check for backups that have failed.
The standard is to enforce policies based on reputable regulatory organizations (e.g. NIST, ACSC) latest recommendations.
You should protect your users and administrator accounts with more than one authentication method.
Do you have Password Writeback enabled in your Entra Connect?
Microsoft Entra Privileged Identity Management (PIM) - formerly Azure Active Directory PIM enables a more secure, manageable and monitorable approach to assigning privileged permissions in your organization.
gMSA (Group Managed Service Accounts) are a secure and practical identity solution from Microsoft where services can be configured to use the gMSA principal and password management is handled by Windows - you don't need to worry about expired passwords anymore.
In an IT industry, there should be a provision to RDP into servers or VMs to access them when needed. Within an organization, it is easier to remotely access laptops or computers connected to the same network.
To RDP, enable Remote desktop in settings How to enable Remote Desktop. Windows has Microsoft Remote desktop connection application inbuilt to RDP to another computer.
Drawbacks of using Microsoft Remote Desktop Connection
- Every time you need to RDP, you have to manually type the IP address or computer name
- List of IPs or device names is not available
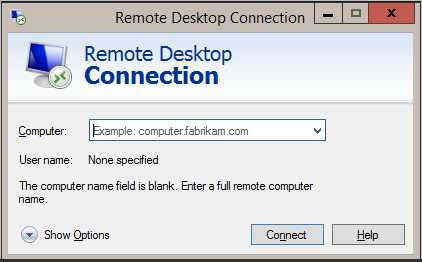
❌ Figure: Bad example - Default Remote Desktop Connection
Solution
Devolution is a secure website that offers a free Remote Connection Management called "Remote Desktop Manager", which is built to centralize all remote connections on a single platform that is securely shared between users and across the entire team.
Multiple computers can be remotely accessed at the same time and have a good GUI interface
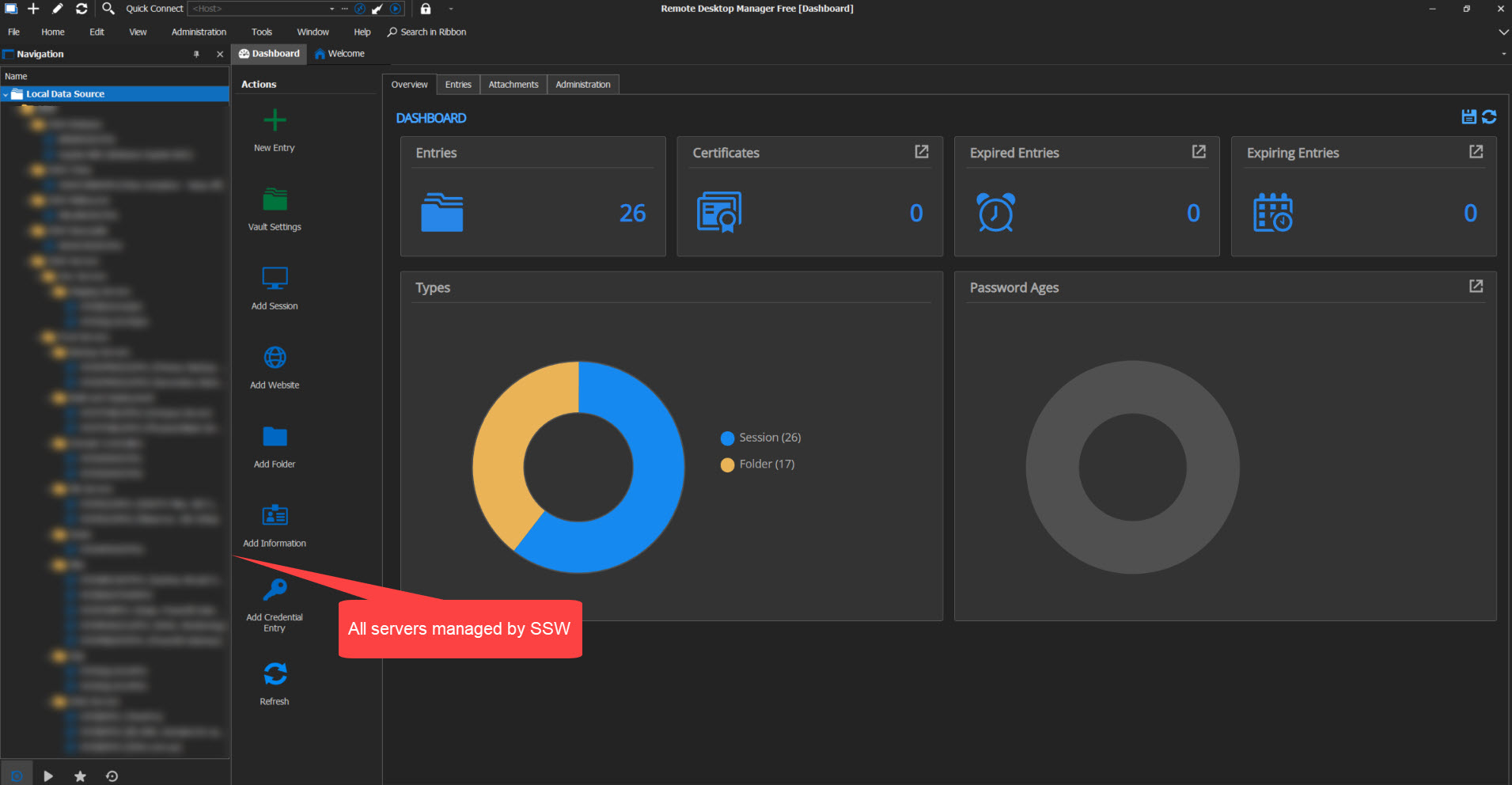
✅ Figure: Good example - Remote Desktop Manager (Devolutions)
To install the application, check devolutions.net
Managing multiple servers and computers located at different locations can be challenging, which is why remote access is often used as a solution. Remote access allows you to remotely log in to a system, making it easier to manage server maintenance.
Windows Hello allows users to sign into their devices using facial recognition, fingerprint, or a PIN, instead of traditional passwords to authenticate quickly, accurately, and securely.
When you fix someone else's PC (locally or remotely), one of the best practices is always make sure it has the latest updates.
It is important that the system administrator can easily find out how reliable his servers are. This can be achieved using tools like What's Up Gold (WUG) https://www.whatsupgold.com to monitor many statistics e.g.:
- Uptime - Ping, Interface monitor
- Performance - RAM usage, CPU usage
- Network - Bandwidth, Interface throughput
- Storage - Disk usage, health
For example, here is a report in WhatsUp Gold you can use to monitor servers on a daily basis.
Do you know if your computer should be joined to the domain or not?
Occasionally, one server and its drives will not have sufficient space to store all related files in a network share. For example, you may have a "SetupFiles" directory that stores all Setup executables on your network e.g. \bee\SetupFiles. There are problems with this approach.
At SSW we have moved away from paid certificates for our websites and web apps. We now use Let's Encrypt managed by Certify The Web.
Previously the way we managed our certificates was using a SharePoint list as well as calendar reminders to inform us when they were going to expire. The issue with using this system is the SharePoint list as well as ensuring the certificates remained up to date was a manual process. This left a lot of room for human error especially when managing hundreds of certificates. There are of course commercial solutions to manage certificates but these haven't been econmical for our environment.
With Certify the Web and Let's Encrypt, we remove this human error and manual handling, ensuring that our certificates never expire.
You should use Certify the Web.
What is the best option for your business when it comes to securing your website with HTTPS?
In Entra ID (formerly Azure AD), App Registrations are used to establish a trust relationship between your app and the Microsoft identity platform. This allows you to give your app access to various resources, such as Graph API.
App Registrations use secrets or certificates for authentication. It is important to keep track of the expiry date of these authentication methods, so you can update them before things break.
Wi-Fi is everywhere now. You can't drive down the street without finding a network which is insecure. However, in an office environment, there is a lot more to lose than a bit of bandwidth. It is vital that wireless is kept secure.
Office Wi-Fi should use WPA3-Enterprise, using RADIUS to securely authenticate users.
per page
1 - 20 of 32 itemsper page
1 - 20 of 32 items